Customers Around the World
internal & external pentest
Test your network
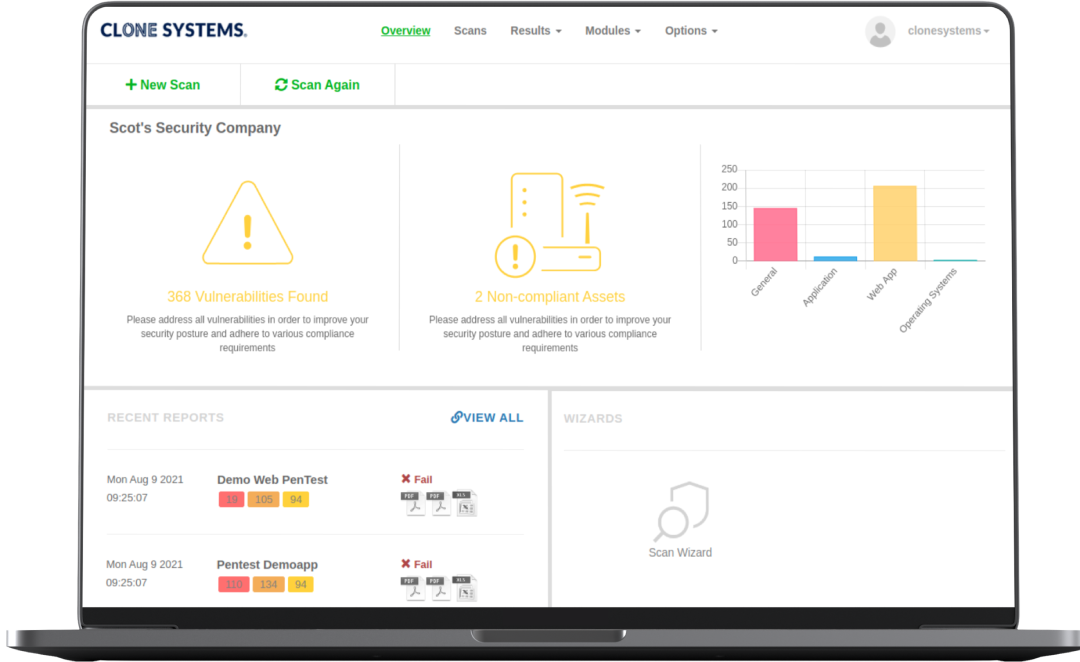
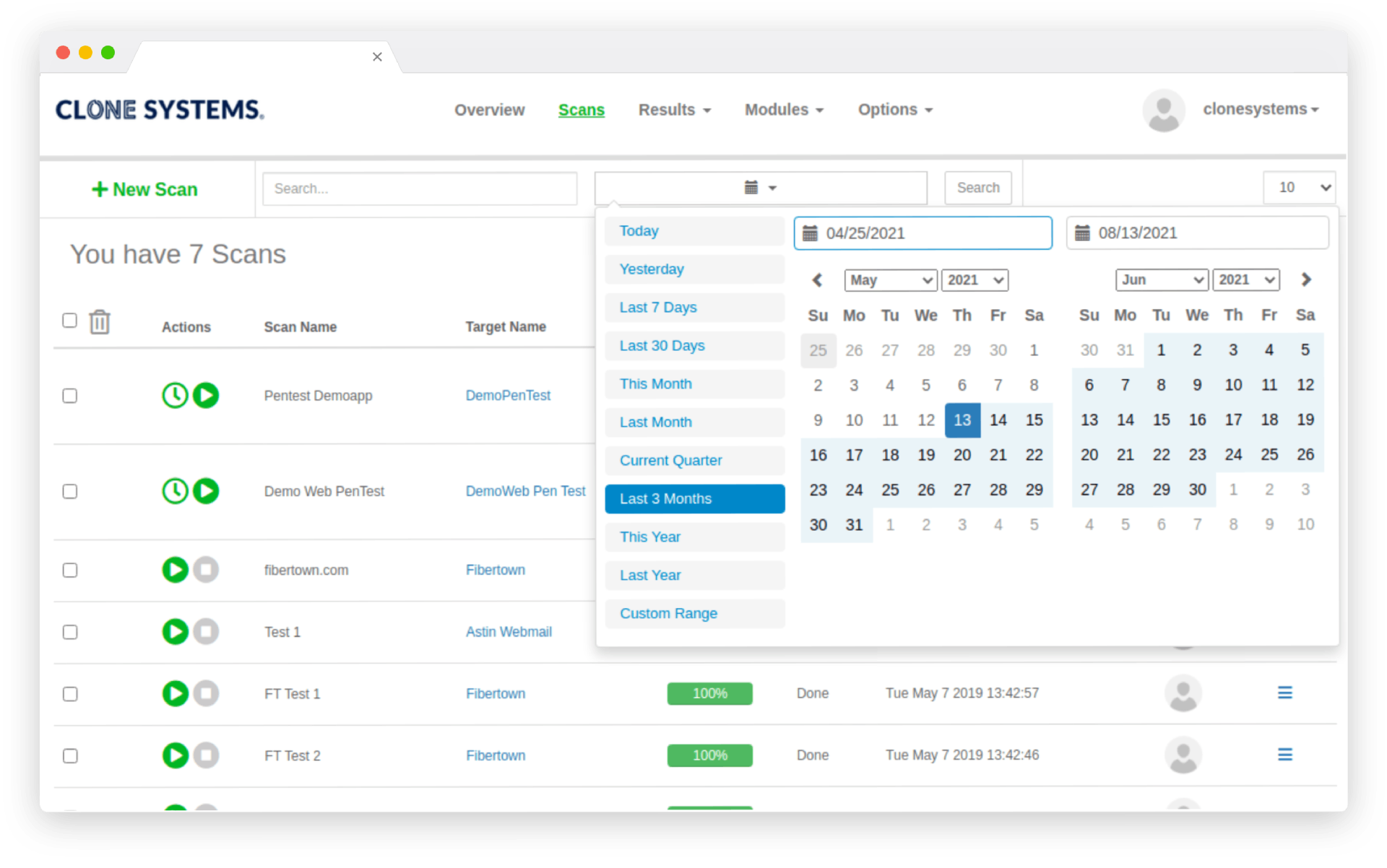
Proactively test your network for vulnerabilities and identify corrective actions. Gain access to an OnDemand web-based portal to conduct self-managed scripted penetration tests. 30-day access to test your network, assess vulnerabilities for security and compliance, remediate, and retest. Perform internal and external penetration testing to meet your business requirements.
exploit vulnerabilities
Improve your security posture
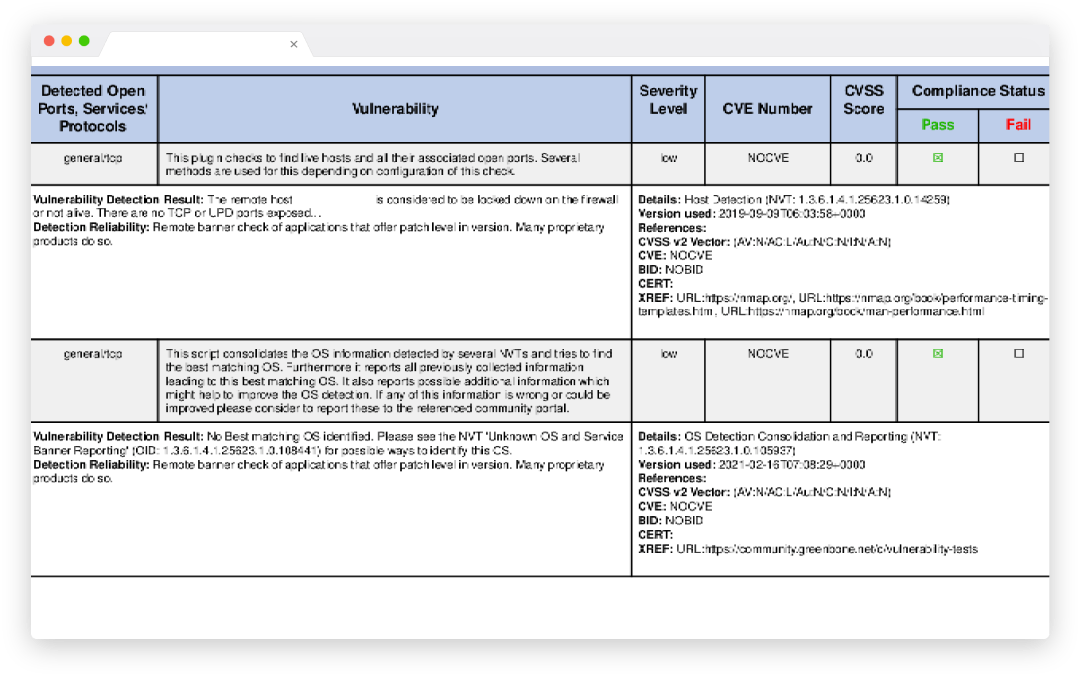
Improve your overall security posture and policies and procedures by understanding the vulnerabilities within your network and how to remediate them. Identify and exploit vulnerabilities by simulating real-world attacks to assess the security posture of your network. Detailed vulnerability report including high, medium, and low vulnerabilities found and exploited, with remediation guidance.
certified reports
Meets compliance requirements
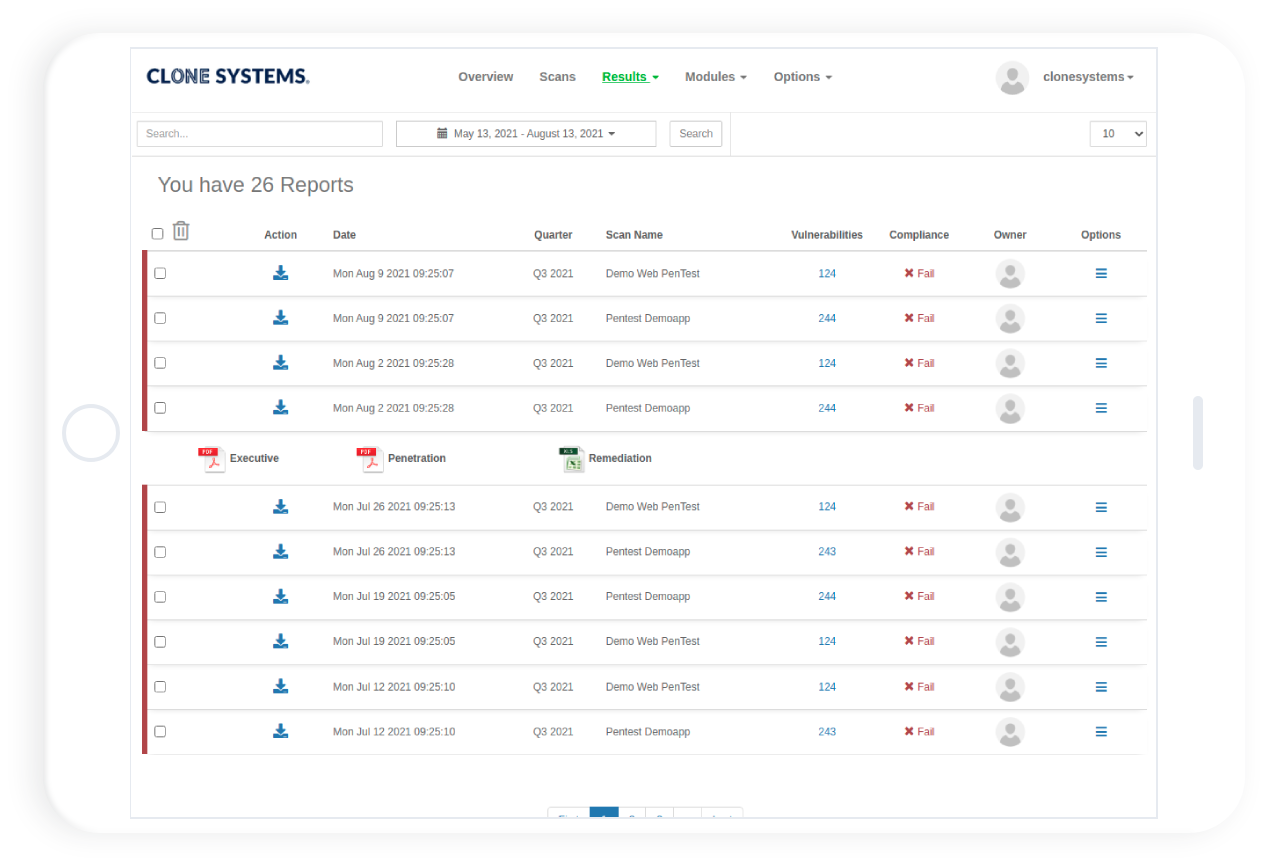
Meets compliance requirements validated by Clone Systems security expertise. Certified pass report after assessing that there are no high or medium vulnerabilities in your environment.
INTERNAL & EXTERNAL PENTEST
Test your network
Proactively test your network for vulnerabilities and identify corrective actions. Gain access to an OnDemand web-based portal to conduct self-managed scripted penetration tests. 30-day access to test your network, assess vulnerabilities for security and compliance, remediate, and retest. Perform internal and external penetration testing to meet your business requirements.
EXPLOIT VULNERABILITIES
Improve your security posture
Improve your overall security posture and policies and procedures by understanding the vulnerabilities within your network and how to remediate them. Identify and exploit vulnerabilities by simulating real-world attacks to assess the security posture of your network. Detailed vulnerability report including high, medium, and low vulnerabilities found and exploited, with remediation guidance.
CERTIFIED REPORTS
Meets compliance requirements
Meets compliance requirements validated by Clone Systems security expertise. Certified pass report after assessing that there are no high or medium vulnerabilities in your environment.
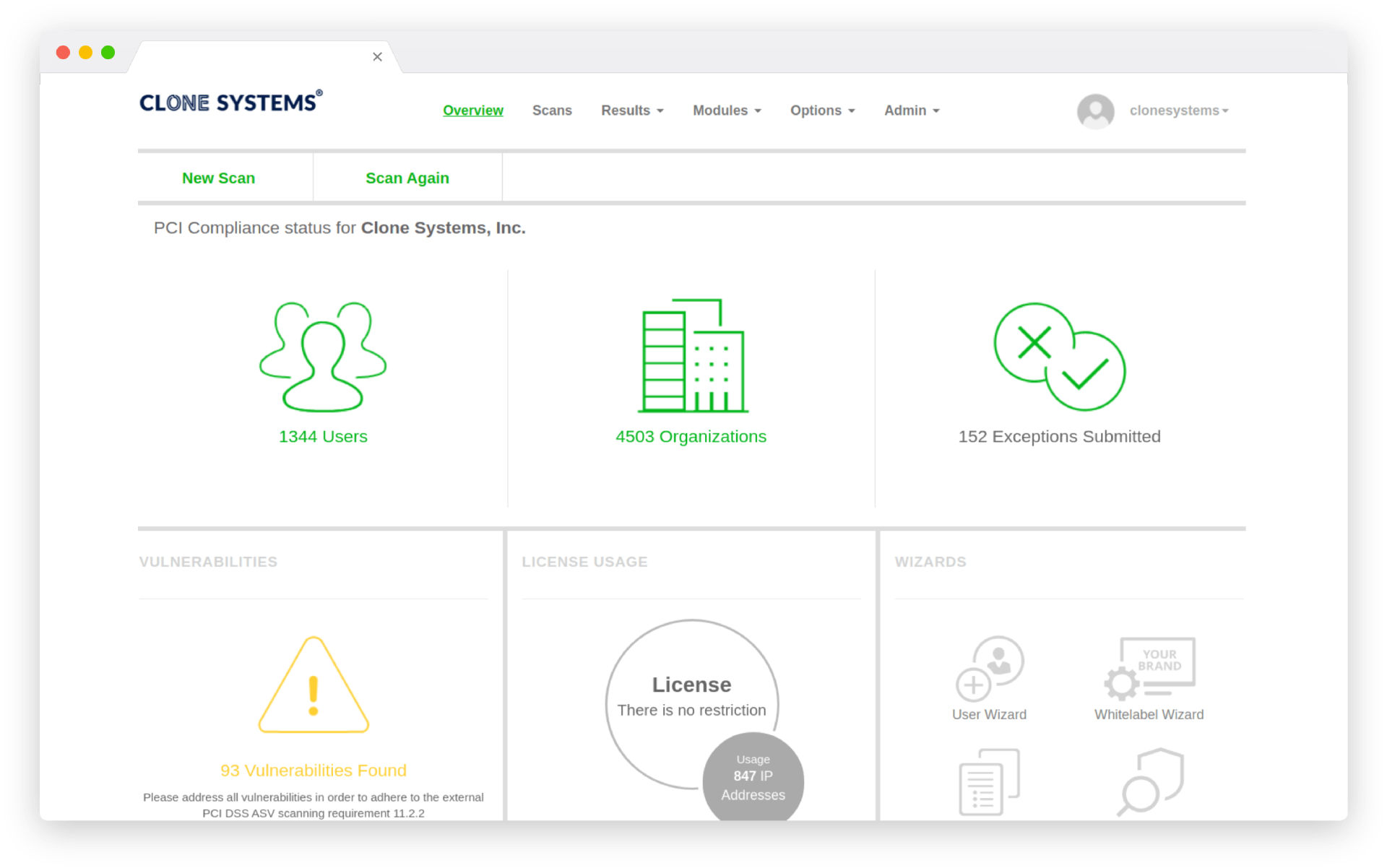
45M+
Vulnerability Checks
Performed Daily
7M+
Vulnerabilities
Uncovered Daily
21K+
Remediations
Performed Weekly
400+
New Signatures
Added Monthly
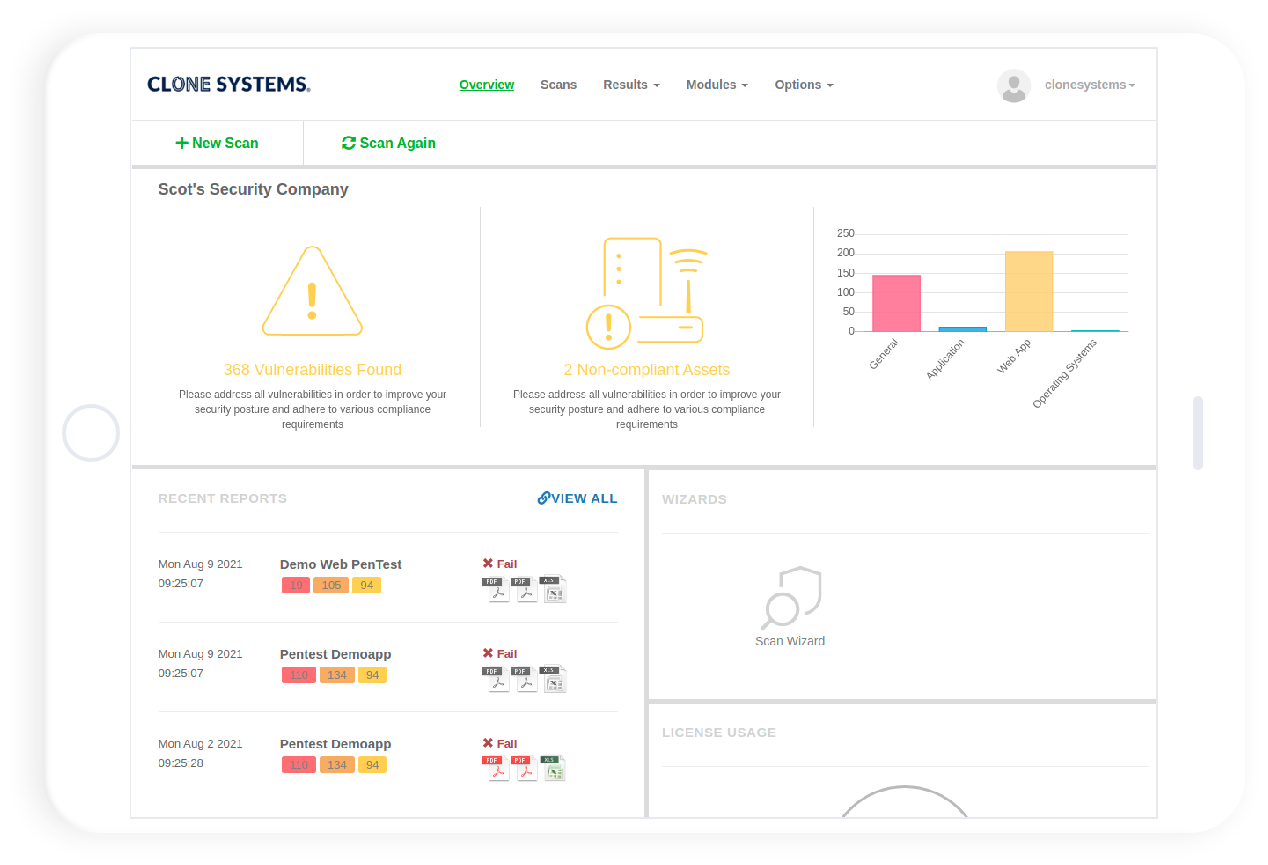
Perform Internal and External Penetration Tests
Perform real-world attack simulations on your infrastructure to identify vulnerabilities and obtain recommendations.
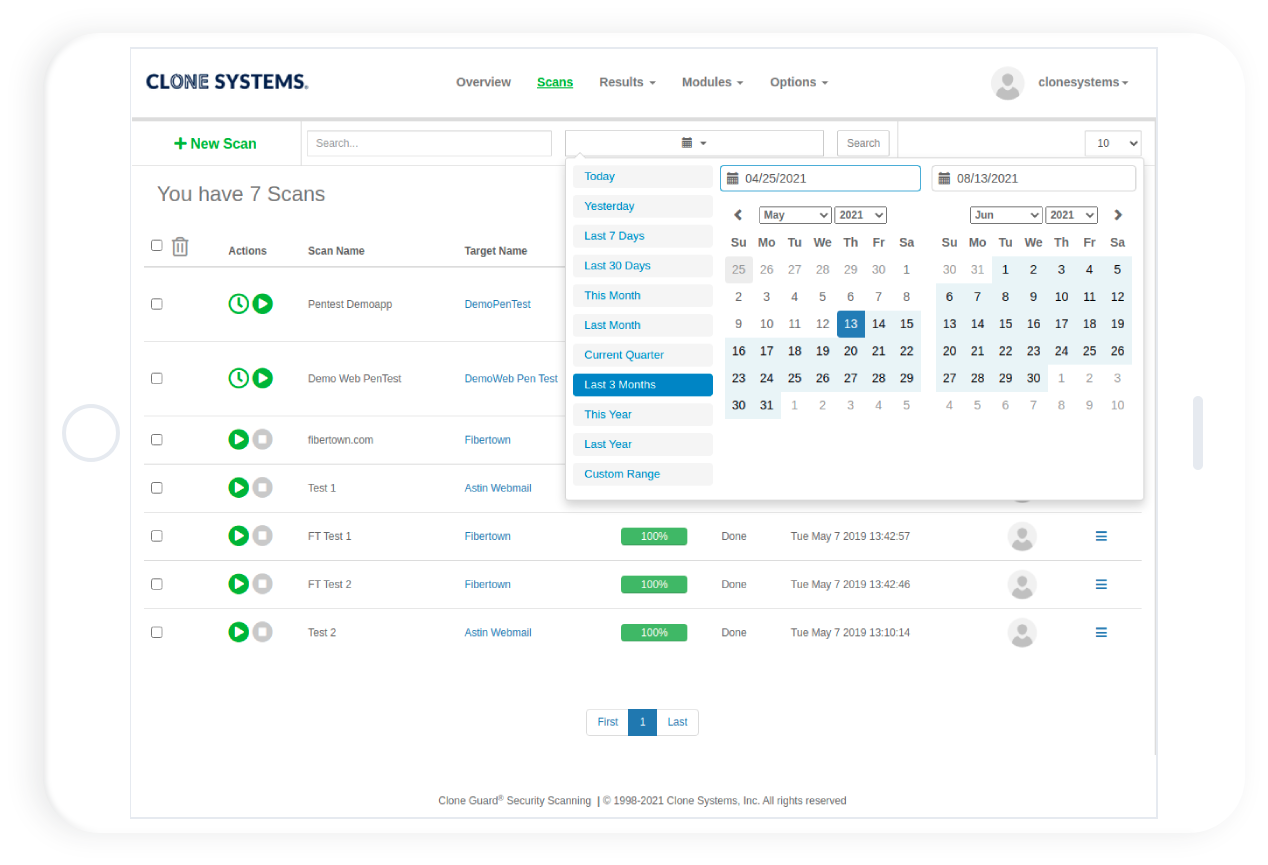

Perform Internal and External Penetration Tests
Perform real-world attack simulations on your infrastructure to identify vulnerabilities and obtain recommendations.
OnDemand web-based portal to conduct penetration tests

Perform internal and external penetration testing

Detailed reports including high, medium, and low vulnerabilities

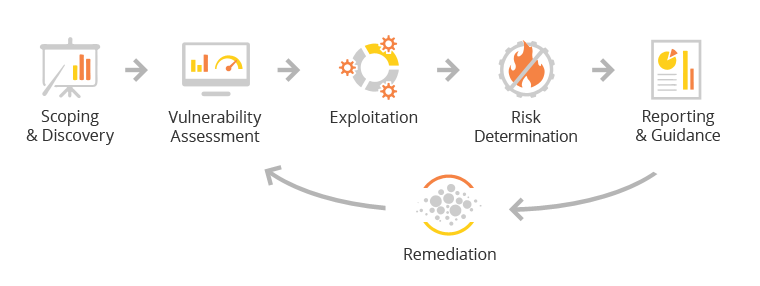
How Automated Scripted PenTest works
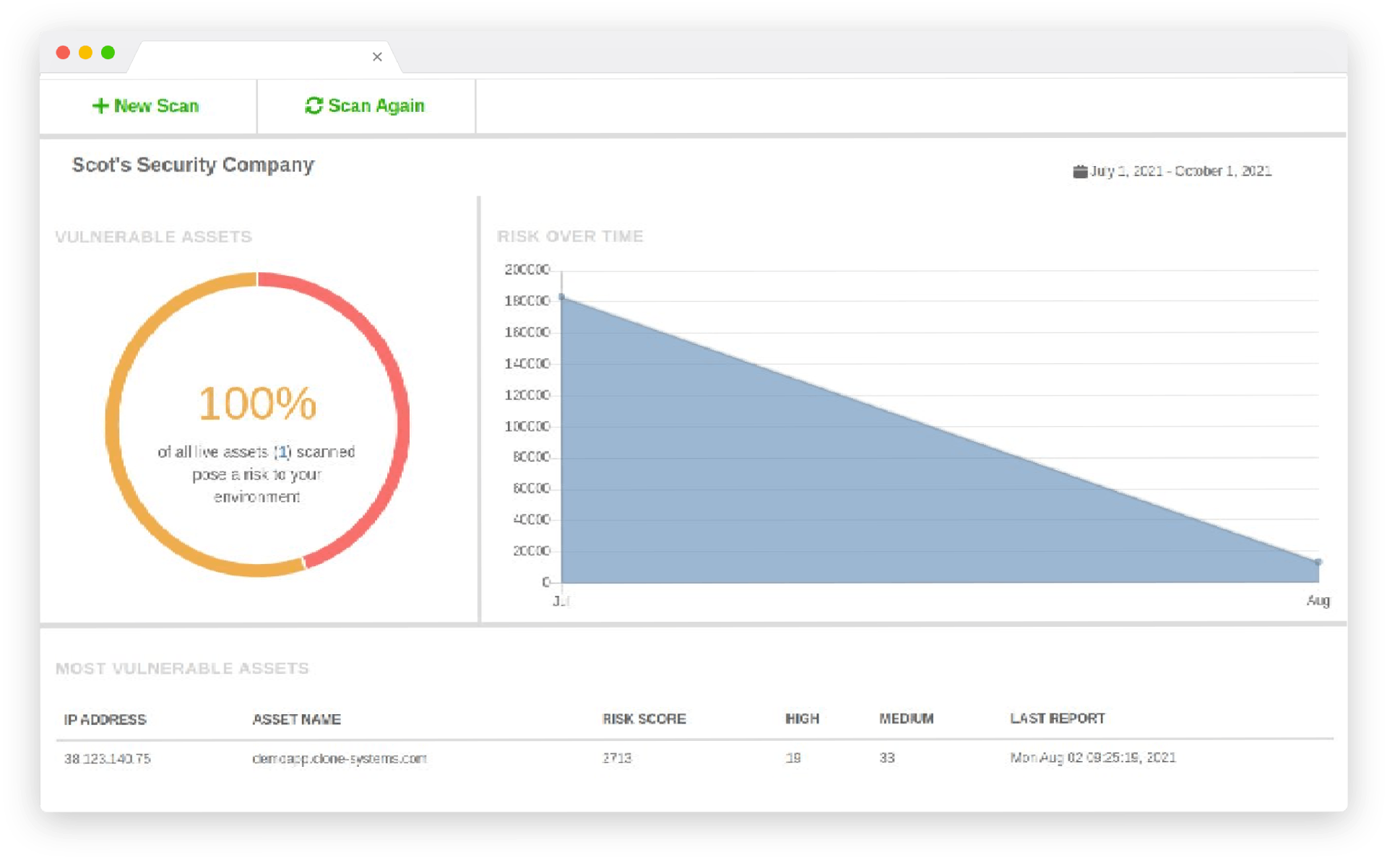
Your team can proactively test your internal and external security controls and assess your infrastructure for vulnerabilities and weaknesses that can be used to compromise and gain unauthorized access to your environment by conducting a self-managed penetration test using a comprehensive security scanning solution with the latest threat intelligence.
A series of real-world attack simulations will be performed against the assets you configure within the solution. Any identified risks or vulnerabilities will be highlighted in a detailed vulnerability report with remediation guidance.
Your team can then work to resolve the findings and then rescan your infrastructure to confirm that any identified security risks and vulnerabilities have been addressed.
Once the assets are secured from all known high and medium vulnerabilities a certified pass report can be accessed and used to meet your audit, regulatory and compliance requirements.
Our battery of security management benchmarks is rigorous and uncompromising. Some of the high-level analysis and performance evaluation stages that are conducted by the OnDemand Penetration testing include the following:
Reconnaissance encompasses passive and active reconnaissance tactics to identify and evaluate your network topology, active hosts, IP addresses, operating systems, open network ports, and all installed security devices.
Analysis entails performing application mapping, network scanning/fuzzing, and vulnerability analysis. It effectively identifies all applications running behind open network ports and their degree of potential vulnerability. The Analysis stage typically involves running SQL Injection, Code Injection, Code Execution, Directory Traversal, and Cross-Site Scripting against the web applications to expose security anomalies.
Penetration employs the data derived from the Analysis stage to exploit your network’s determined weak points to gain access. Typically, the Penetration phase focuses primarily on vulnerabilities revealed for network services and externally facing web applications.
The informational phase generates alerts once a vulnerability has been successfully exploited. A system restore, immediately returns the network to its previous state before the intrusion. In addition, a detailed report is generated on all areas of your enterprise to assess how and why the intrusion was successful.
Finally, the Documentation phase reflects all testing results, all intrusions, the areas of the system that were compromised during an intrusion, intrusion-resistance recommendations, and qualitative analysis reports of each security mechanism employed on your network.

Automated Scripted PenTest Product Sheet
Discover how you can assess your security posture with the automated Clone Guard On-Demand PenTest.