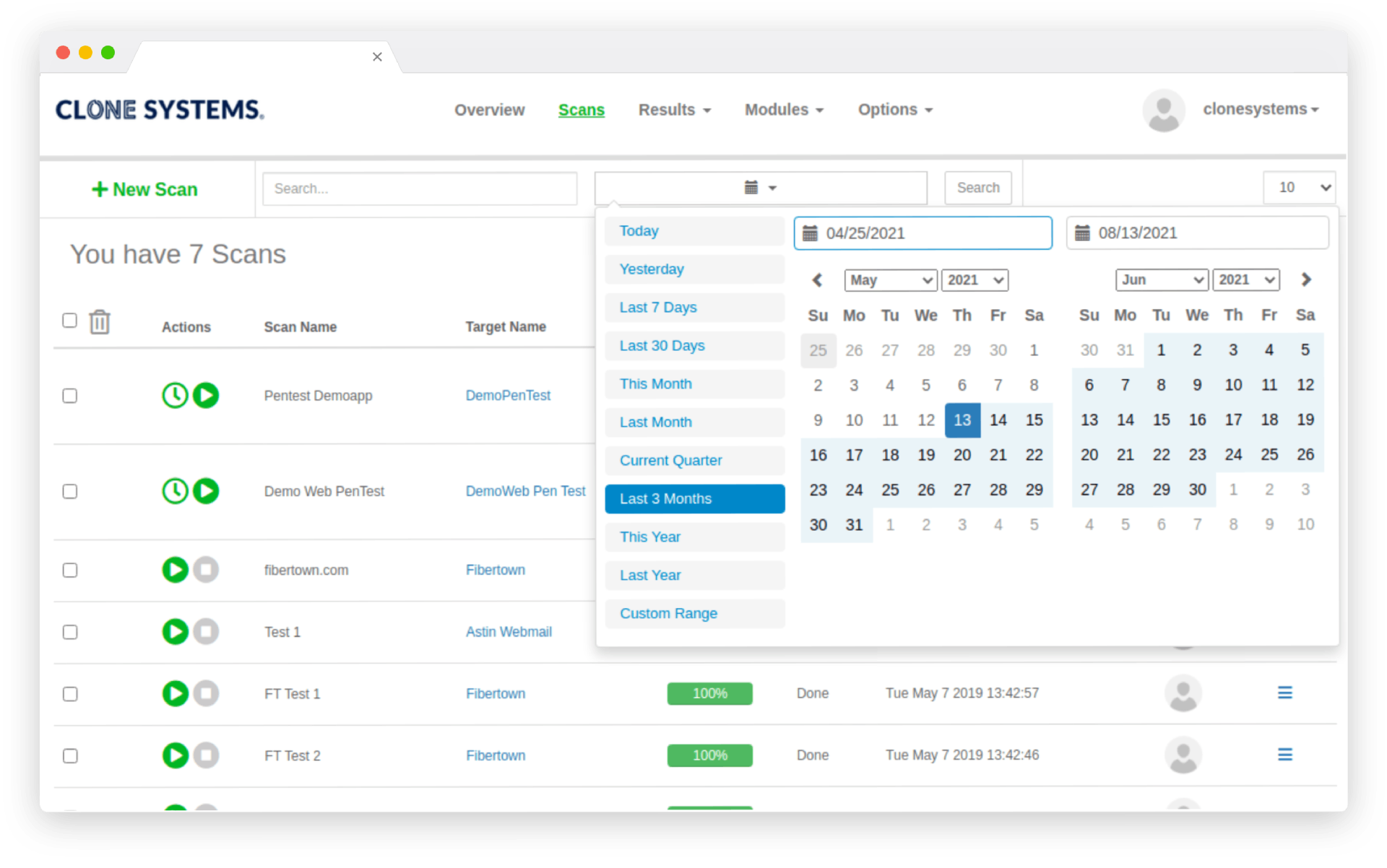
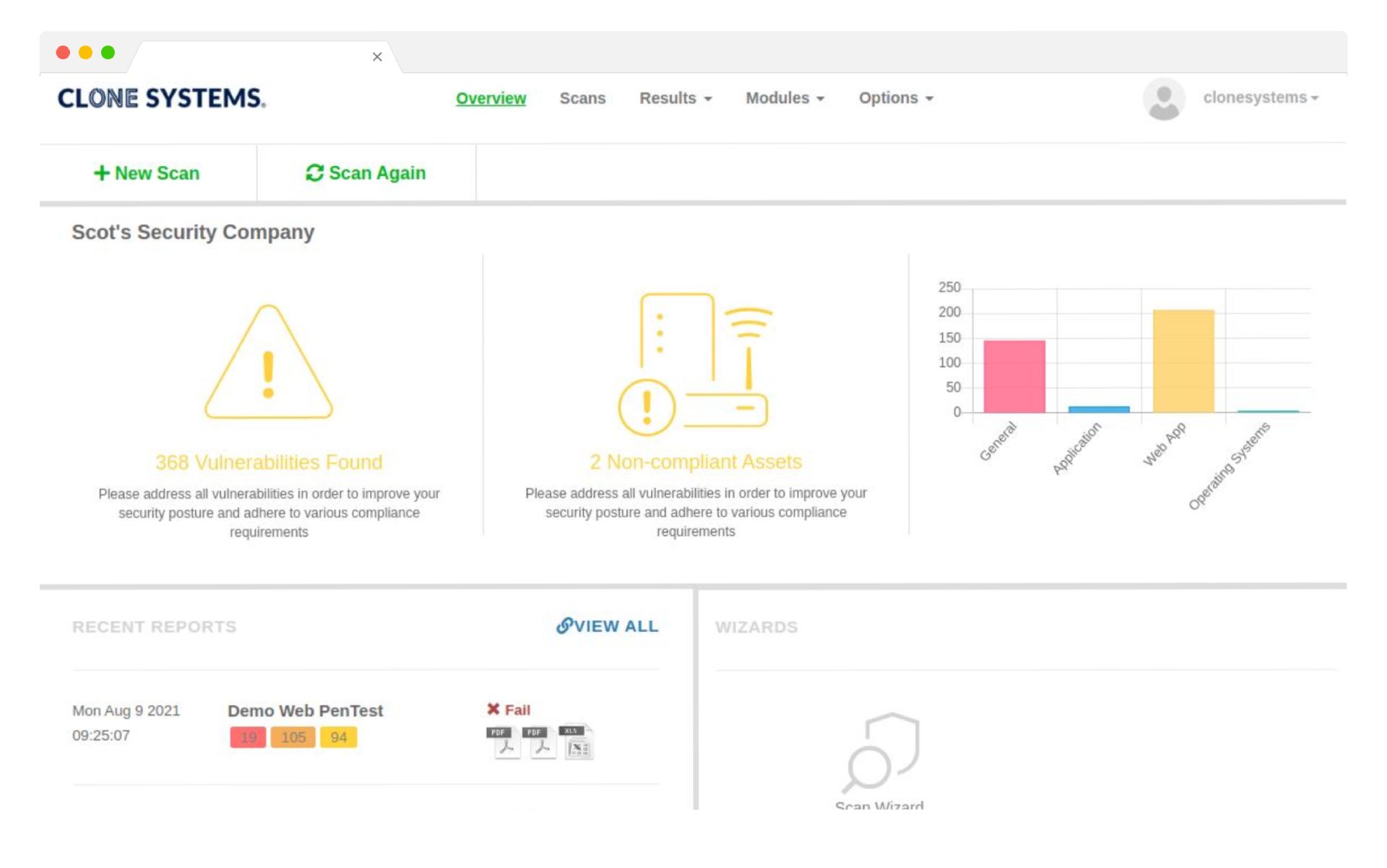
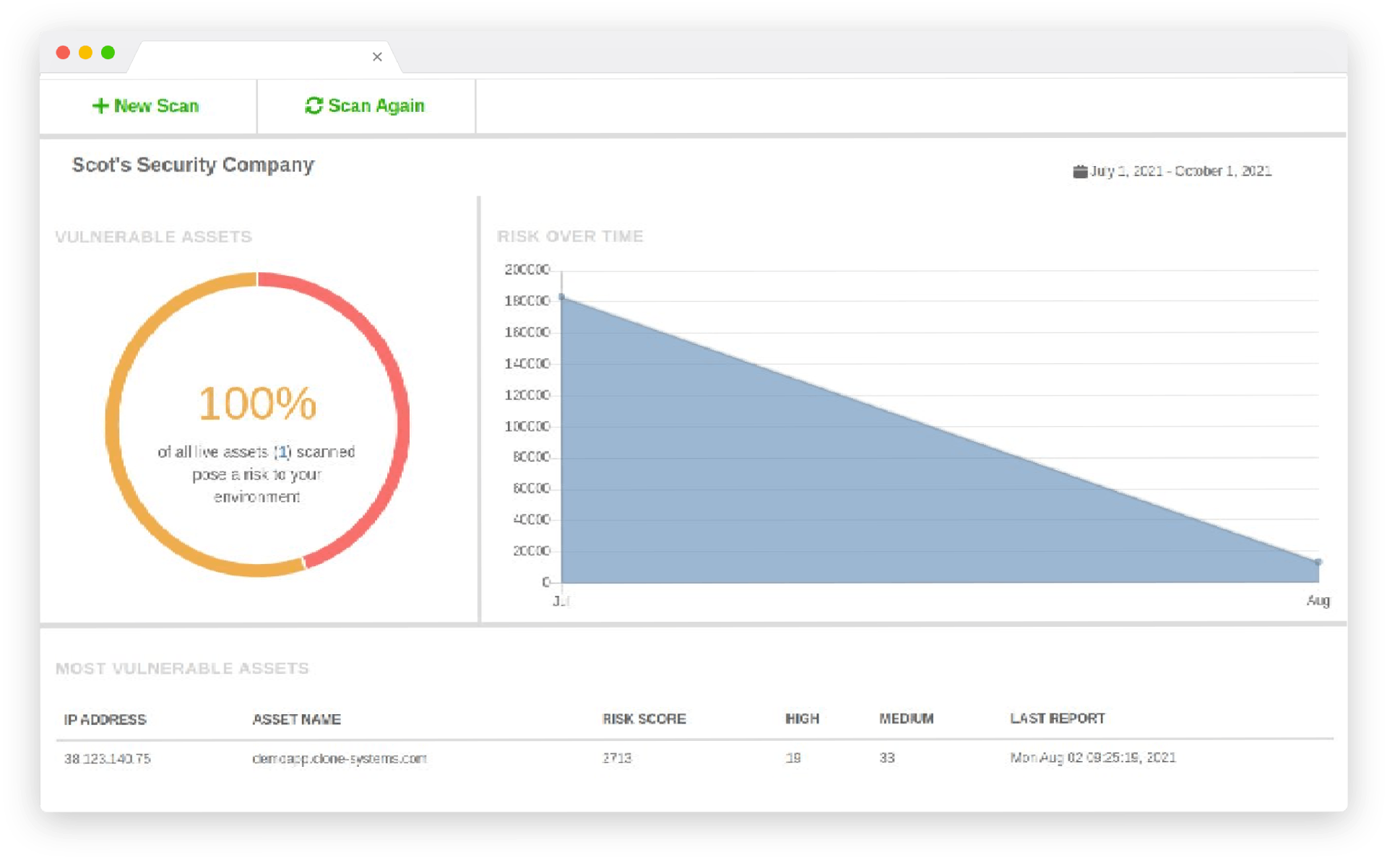
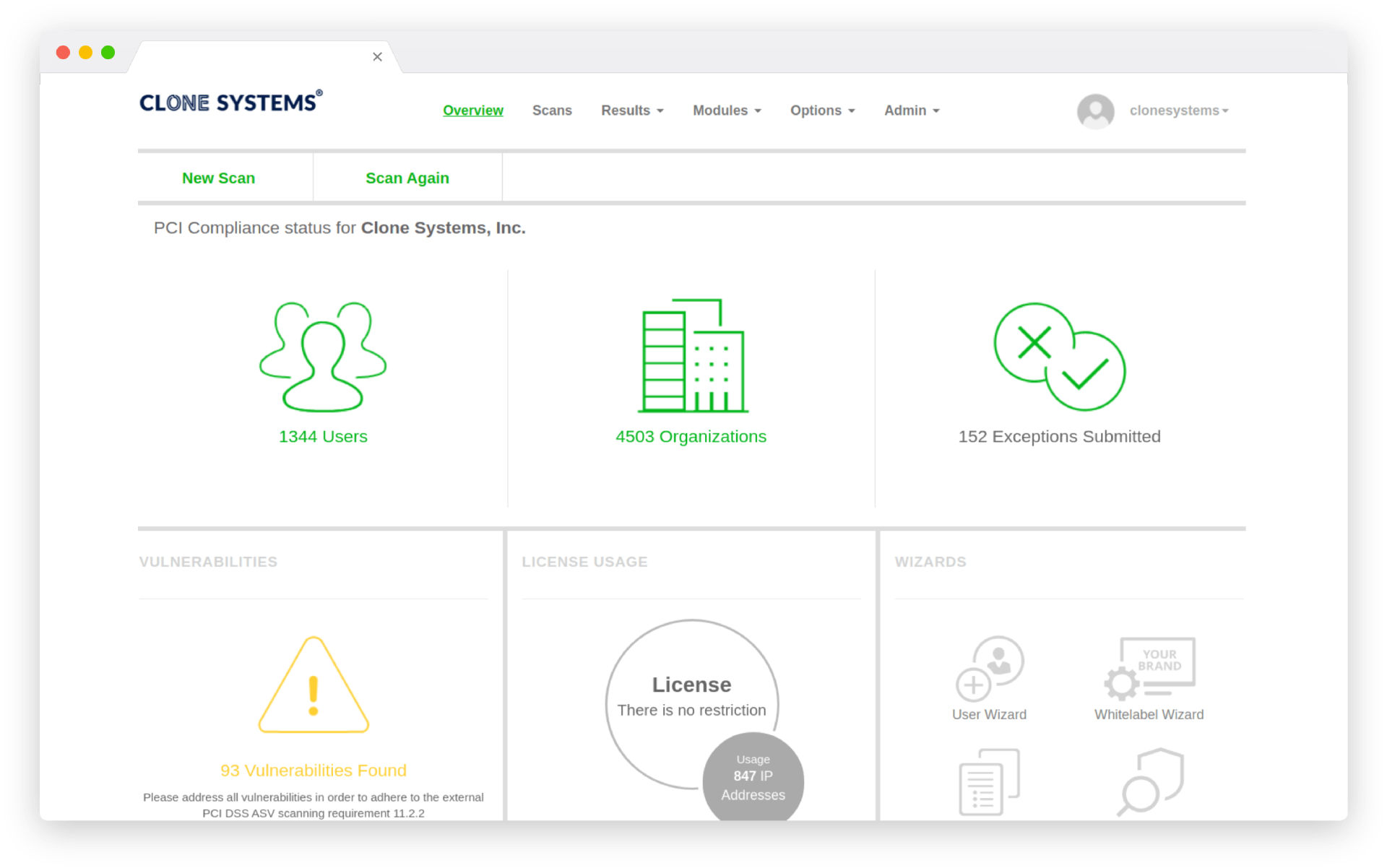
Managed Penetration Testing
One our our CISSP Engineers will perform real-world attack simulations on your infrastructure to identify threats
Talk with our experts
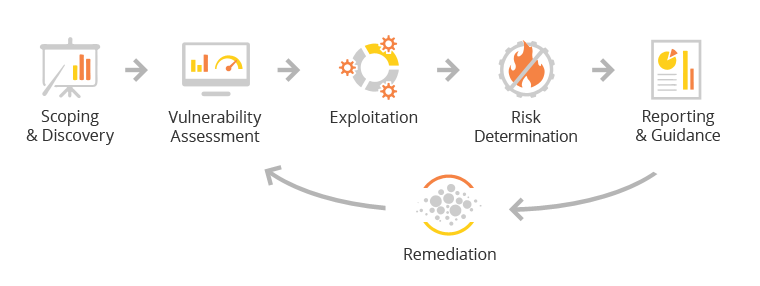

Managed Penetration Testing
One our our CISSP Engineers will perform real-world attack simulations on your infrastructure to identify threats
Customers Around the World
Obtain support and guidance
Obtain support, education, and guidance from a certified security engineer on how to improve your network. Our CISSP Engineers have extensive experience assessing security and compliance vulnerabilities. Detailed vulnerability report including high, medium, and low vulnerabilities found and exploited with remediation guidance and recommendations.
Improve your security posture
Improve your overall security posture and your policies and
procedures by understanding the vulnerabilities within your
network and how to remediate them.
Meet compliance requirements
Meet and exceed audit, regulatory, and compliance requirements validated by Clone Systems security expertise. Receive a certified pass report after assessing that your environment has no high or medium vulnerabilities.
*OnDemand Penetration testing is available if you want your team to conduct the scan.
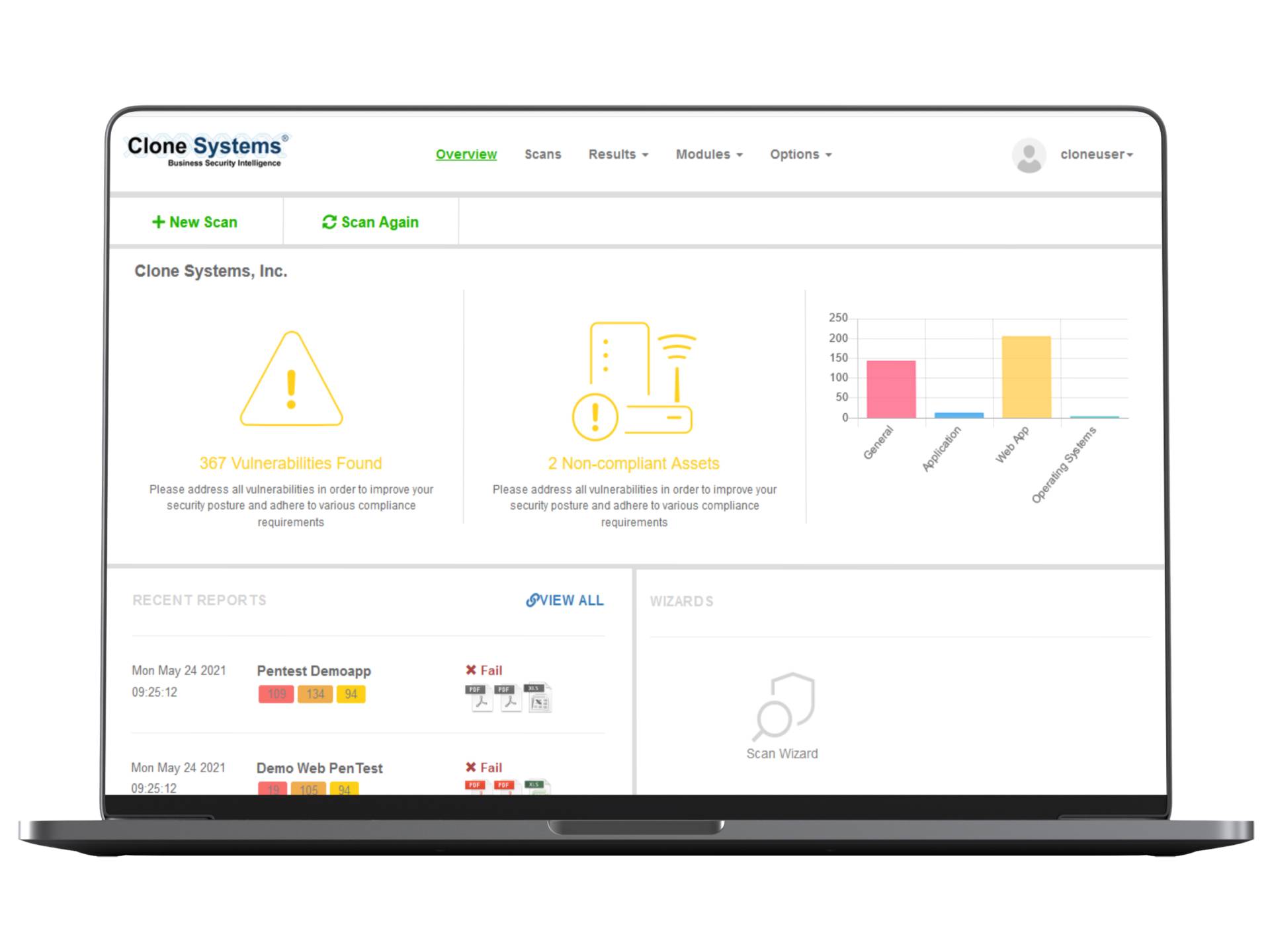
Obtain support and guidance
Obtain support, education, and guidance from a certified security engineer on how to improve your network. Our CISSP Engineers have extensive experience assessing security and compliance vulnerabilities. Detailed vulnerability report including high, medium, and low vulnerabilities found and exploited with remediation guidance and recommendations.

Improve your security posture
Improve your overall security posture and your policies and procedures by understanding the vulnerabilities within your network and how to remediate them.

Meet compliance requirements
Meet and exceed audit, regulatory, and compliance requirements validated by Clone Systems security expertise. Receive a certified pass report after assessing that your environment has no high or medium vulnerabilities.
*OnDemand Penetration testing is available if you want your team to conduct the scan.

Product Sheet
Discover how you can improve your security posture with the Clone Guard Managed Penetration Testing Product Sheet.