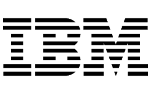Dark Web Probing
Use the Dark Web Probing service to detect if your company’s sensitive data has been exposed on the dark web.
Talk with our experts

Dark Web Probing
Use the Dark Web Probing service to detect if your company’s sensitive data has been exposed on the dark web.
Talk with our experts
Customers Around the World
avoid targeted assaults
Reduce Your Risk of a Data Breach
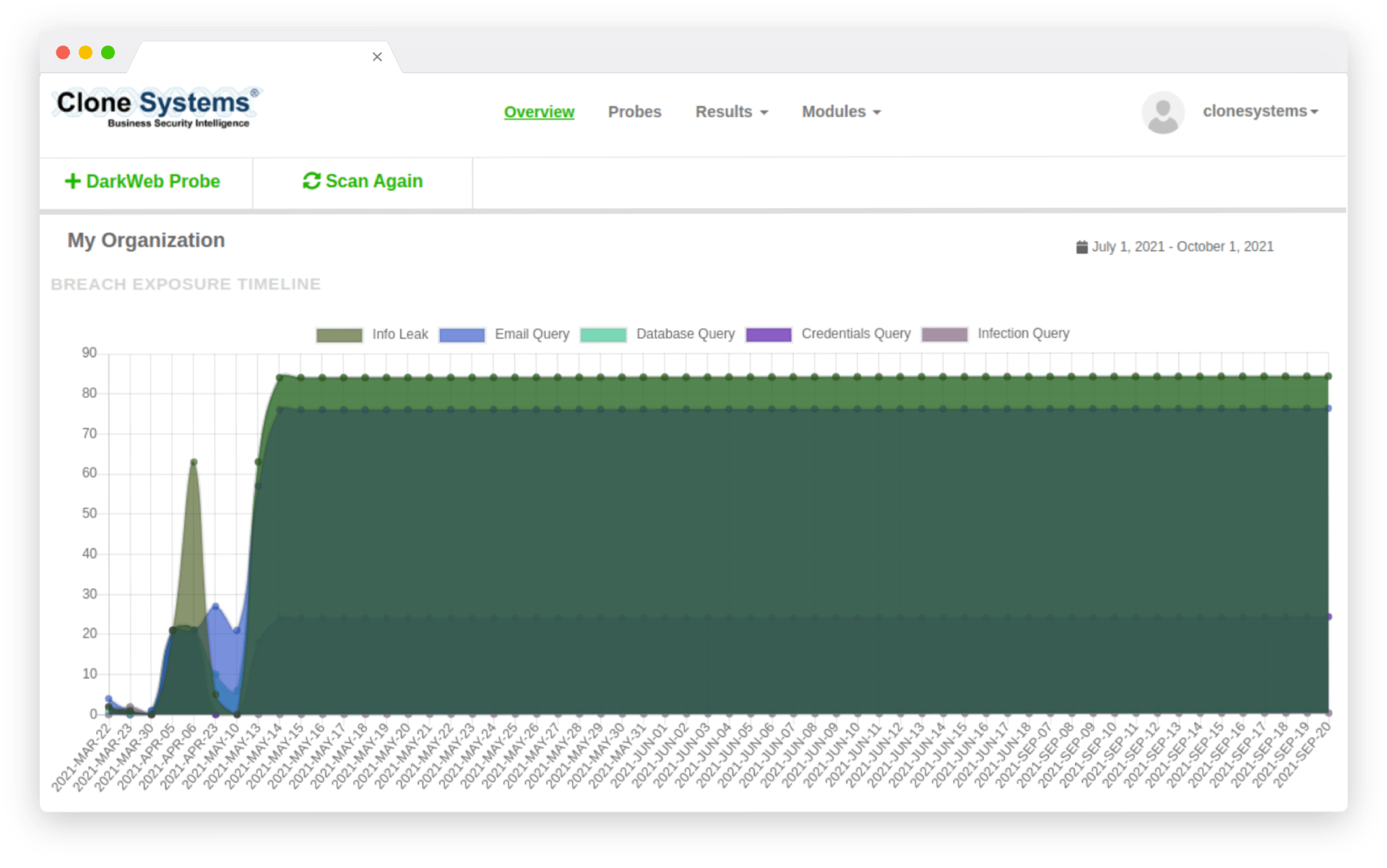
Employee account takeover occurs when hackers use stolen logins to access company accounts. When employees reuse passwords across several internet accounts, thieves can access business accounts using credentials disclosed in third-party data breaches. Detect and reset compromised passwords before criminals can exploit them early to help organizations avoid account takeover and targeted assaults like ransomware.
protect sensitive data
Preventing Account Takeover
Detect and recover compromised credentials early in the breach timeframe, before focused account takeover attacks normally start. Infiltrate criminal networks to recover data before it becomes public, allowing businesses to protect sensitive personnel and limit entry points.
get alerted for data breaches
Protect Your Customers
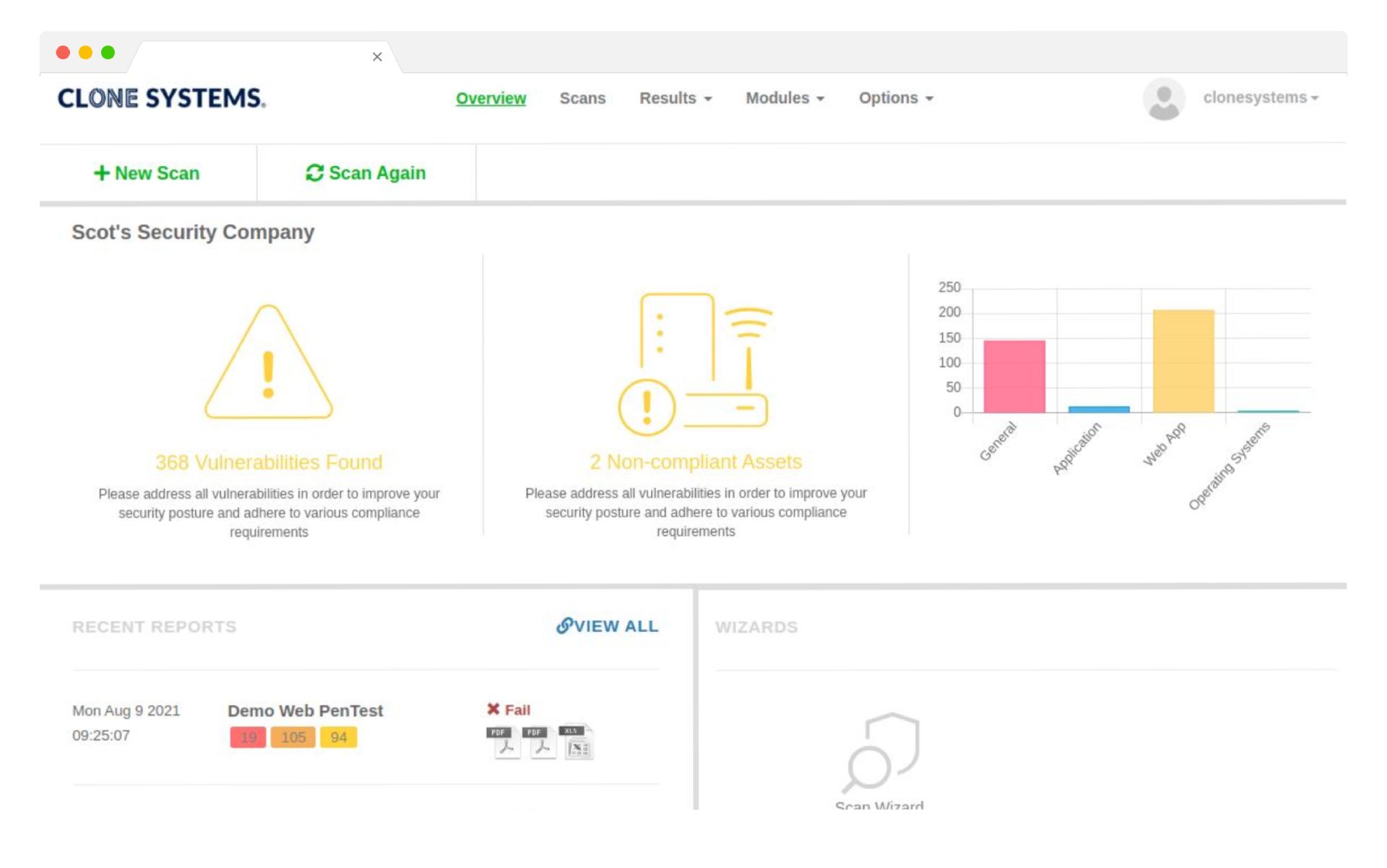
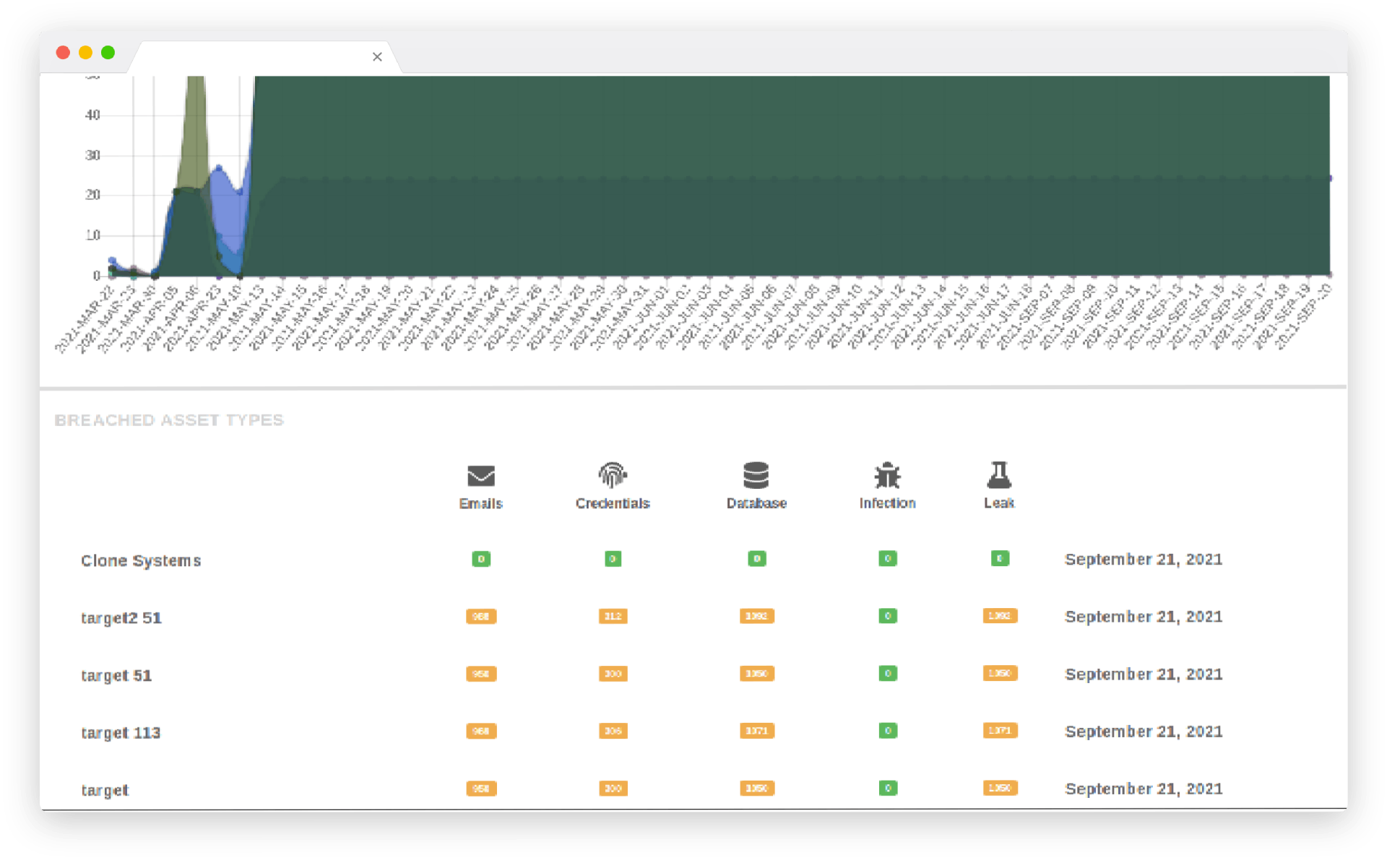
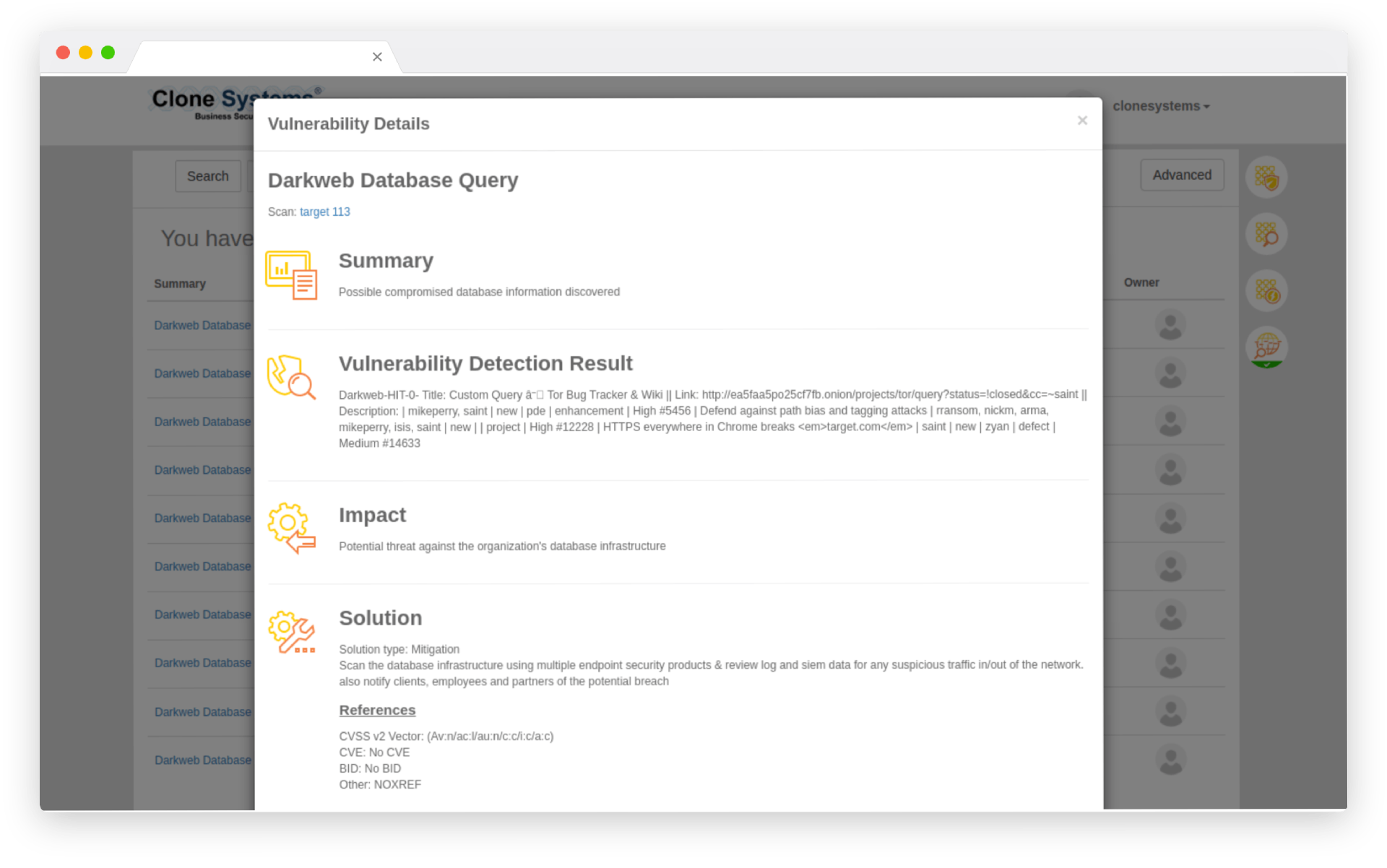
Detect and remediate stolen company information before bad actors use them. Check your company’s proprietary information against the world’s largest repository of recovered breach assets, and get alerted if any signs of a breach could put your customers at risk.
AVOID TARGETED ASSAULTS
Reduce Your Risk of a Data Breach
Employee account takeover occurs when hackers use stolen logins to access company accounts. When employees reuse passwords across several internet accounts, thieves can access business accounts using credentials disclosed in third-party data breaches. Detect and reset compromised passwords before criminals can exploit them early to help organizations avoid account takeover and targeted assaults like ransomware.
PROTECT SENSITIVE DATA
Preventing Account Takeover
Detect and recover compromised credentials early in the breach timeframe, before focused account takeover attacks normally start. Infiltrate criminal networks to recover data before it becomes public, allowing businesses to protect sensitive personnel and limit entry points.
GET ALERTED FOR DATA BREACHES
Protect Your Customers
Detect and remediate stolen company information before bad actors use them. Check your company’s proprietary information against the world’s largest repository of recovered breach assets, and get alerted if any signs of a breach could put your customers at risk.

What is Dark Web Probing, and how does it work?
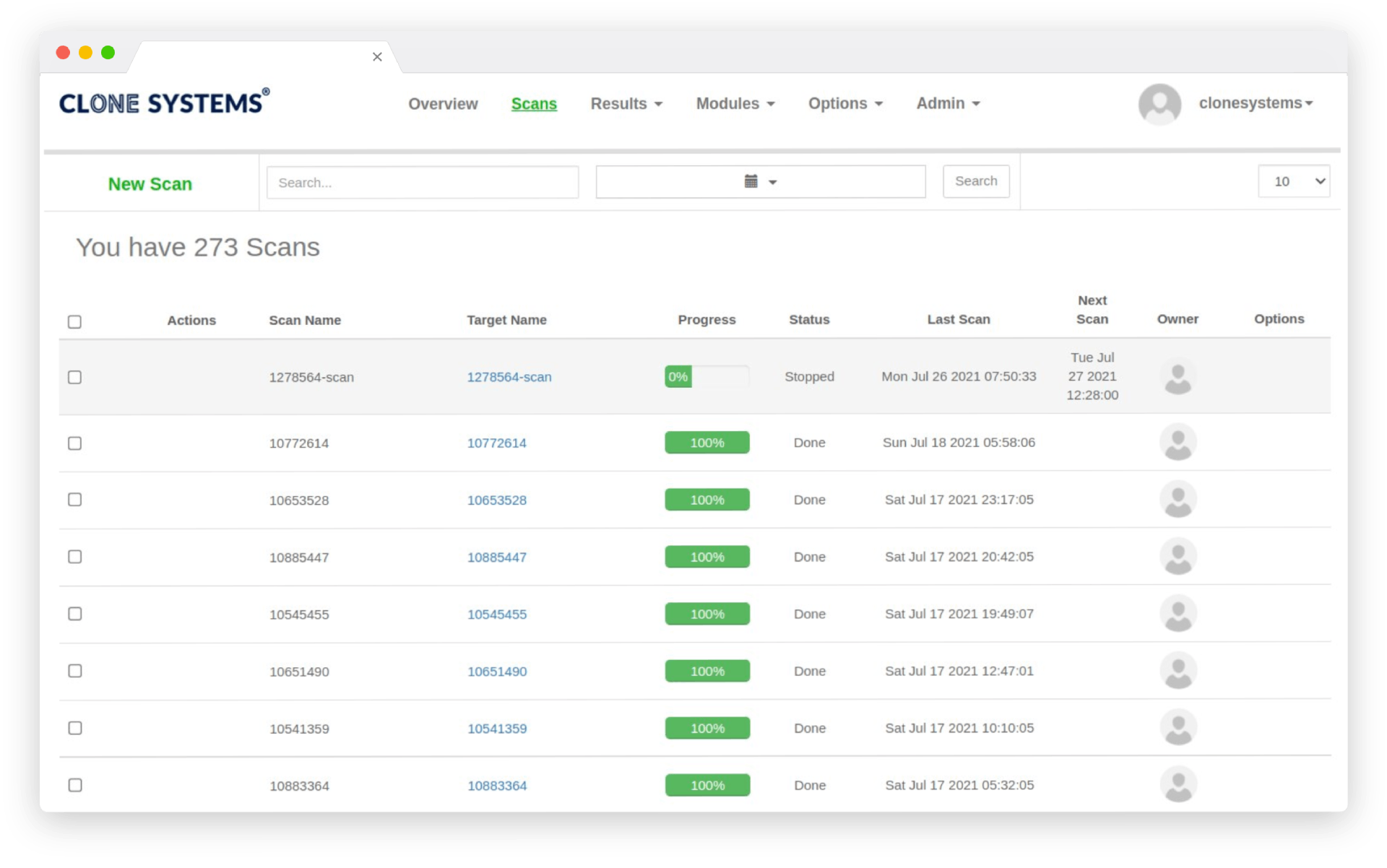
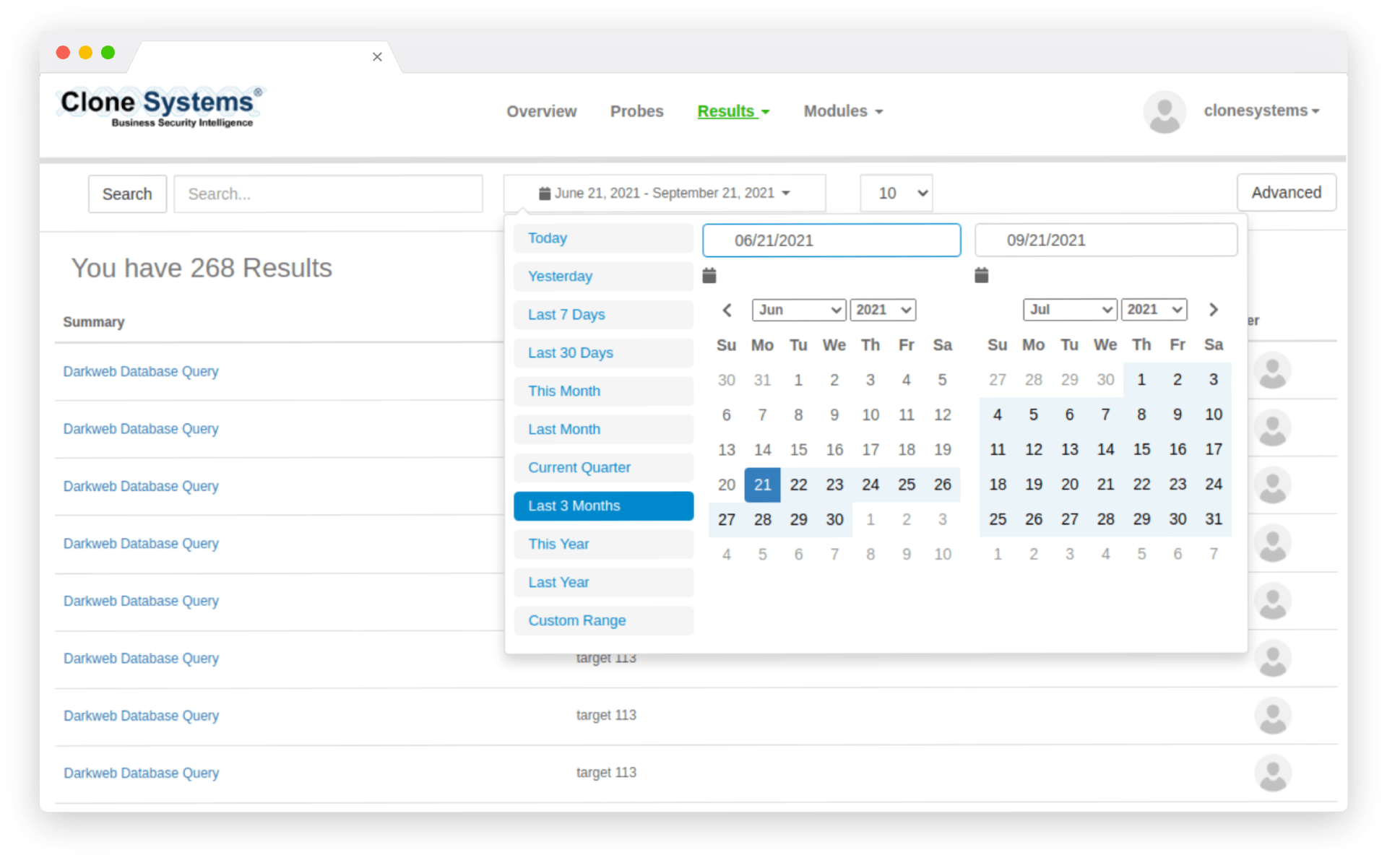
Dark web probing and monitoring are searching for and tracking company data on a portion of the internet that is not ordinarily accessible by end-users.
Access to the dark web is via unique API connectivity. It’s hidden from search engines and hides IP addresses. The dark web’s privacy and anonymity attract those seeking to remain hidden, whether for personal or criminal reasons, including identity theft. If your Social Security number or other identifying information is stolen, it may be sold on the dark web to a fraudster. Dark web monitoring can help protect your company’s reputation and, thus, your finances.
Every day, our dark web monitoring service scans millions of suspicious entry points to identify any stolen information. This includes Social Security numbers, Email addresses, Passport numbers, Medical identification numbers, Bank account numbers, Phone numbers, Driver’s licenses, Credit/debit cards, Retail/membership cards, backdoors, credentials, etc.