MCP Servers in Agentic AI: What They Are and How to Secure Them
The rise of agentic AI has brought forward infrastructure constructs not seen a few years ago. One such construct is the MCP server, part of the Model Context Protocol (MCP) ecosystem. As organizations adopt AI agents capable of acting on external systems, MCP servers take on a pivotal role as gateways and potential risk vectors. In this article I explain what MCP servers are, highlight major security threats, and offer best practices for protecting them in environments where compliance matters.
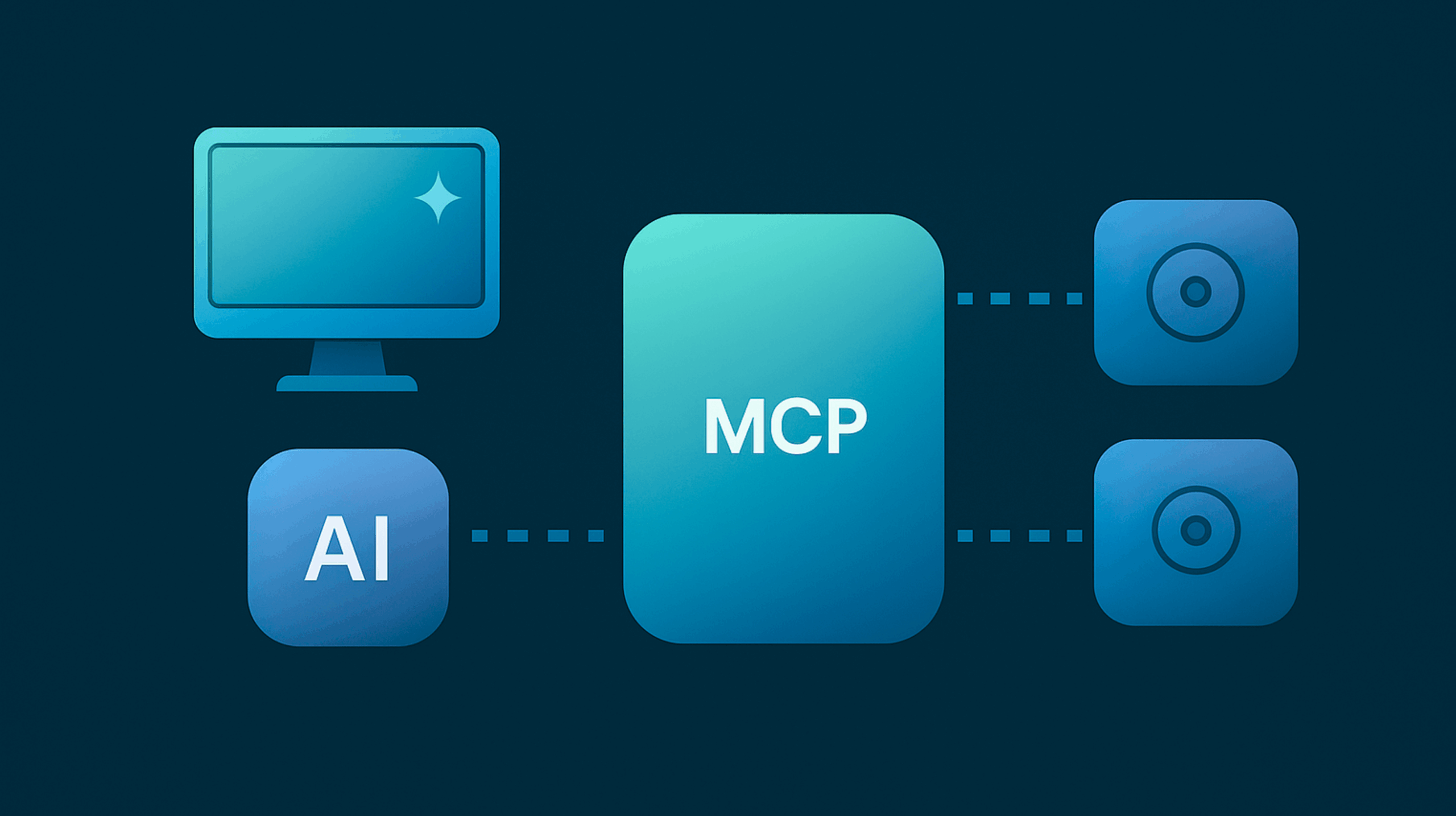
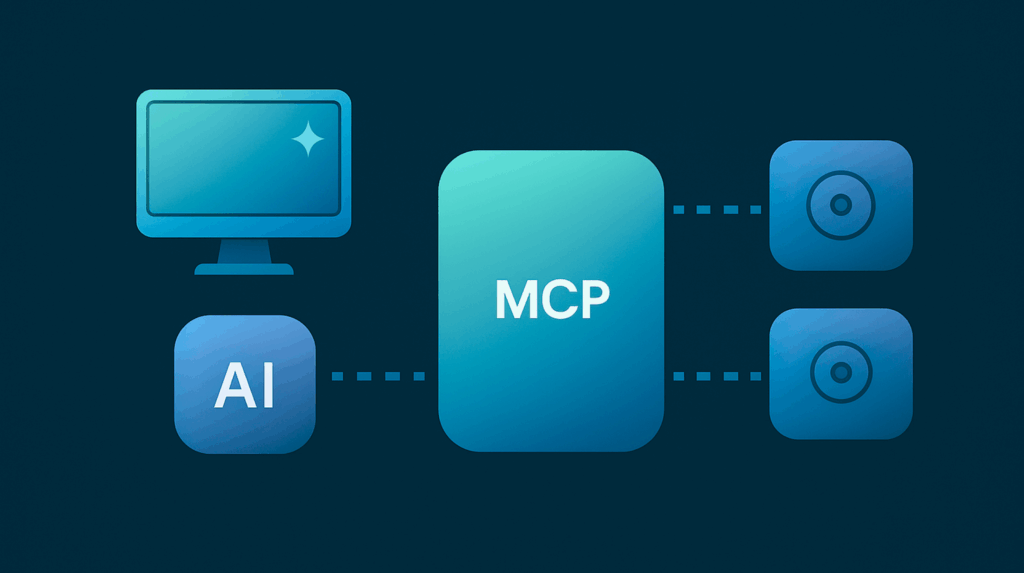
What Is an MCP Server?
The Model Context Protocol is an open standard introduced by Anthropic in late 2024 that enables AI systems (clients) to connect to external tools, data sources, or business logic in a structured and secure fashion.
An MCP server acts as an intermediary between an AI agent and external systems. The AI agent sends structured requests to the MCP server. The server then invokes APIs, queries databases, reads or writes files, or triggers workflows and returns the results. The agent never directly interfaces with the underlying systems.
By structuring all interaction through this interface, the MCP server is the central point for authentication, authorization, logging, and validation. This architecture is powerful. If not secured properly, however, it can become an exploitation path.
Key Security Risks to Be Aware Of
Because MCP servers mediate access between agents and business resources, they introduce new threats that must be addressed. The following risk categories deserve particular attention.
Token Theft and Credential Abuse
MCP servers frequently hold OAuth or API tokens that grant broad access to downstream systems. If an attacker compromises the MCP server, they may retrieve these tokens and act on behalf of the agent or user. Many of those actions occur via APIs, and may not generate alerts associated with user logins.
Prompt Injection and Tool Manipulation
AI agents interpret natural language prompts before converting them into structured requests. Malicious prompts can influence which tools are selected. This kind of attack is known as prompt injection. In addition, definitions, metadata, or descriptions of tools may be tampered with (a practice sometimes called tool poisoning), causing the agent to invoke harmful operations under the guise of benign tools.
Rogue or Fake MCP Servers
Because MCP authentication models are still maturing, attackers may deploy counterfeit MCP servers that mimic legitimate ones. If an agent connects to one of these malicious endpoints, credential interception, request redirection, or silent data extraction may result.
Cross-Tool Exfiltration and Trust Chaining
A single MCP server may expose multiple tools or capabilities. If compromised, it can abuse trust relationships to move laterally, chain across tools, or exfiltrate data. Research has demonstrated that even minimal “Trojan” MCP servers can exploit tool chaining to steal sensitive information.
Identity Fragmentation and Audit Challenges
Many MCP implementations struggle with identity fragmentation. The system may fail to consistently map each request or tool invocation to a specific agent or session. This weakens accountability and complicates forensic investigation. Audit logs might record actions but lack clear attribution, creating blind spots during incident response.
Preference Manipulation Attacks
A growing class of attacks, called Preference Manipulation Attacks, demonstrates how adversaries can craft tool names or descriptions that encourage agents to prefer a malicious MCP server over a legitimate one. This subtle engineering shifts agent behavior toward compromised infrastructure without immediate detection.
Best Practices to Secure MCP Servers
Securing MCP servers requires a multi-layered defense strategy. Below are recommended practices to adopt:
Strong Authentication and Authorization
Employ mutual TLS, token binding, or OAuth with strict audience and scope restrictions when agents connect to MCP servers. Avoid static credentials. Use fine-grained permission models so agents access only the tools they require.
Tool Whitelisting and Integrity Verification
Do not accept dynamic tool definitions without rigorous review. Explicitly whitelist only trusted tools. Require cryptographic signatures or integrity checks on tool metadata or binaries so tampering can be detected.
Input Validation and Execution Safety
Validate and sanitize all requests from agents before execution. Avoid shell escapes and unchecked parameters. When feasible, execute tools in sandboxes or isolated environments so that any misbehavior cannot compromise the server or other tools.
Logging, Monitoring, and Alerting
Log every tool invocation, input, output, error, and associated metadata. Link logs to agent identities or session tokens. Use anomaly detection to surface unusual tool usage or behavior. Protect logs from tampering.
Supply Chain Protections
Verify the origin, integrity, and trustworthiness of MCP servers or tool packages before deployment. Limit accepted registries or package sources to trusted repositories. Maintain internal mirrors or curated registries when possible.
Regular Penetration Testing and Threat Modeling
Include MCP components in security audits and red team engagements. Simulate attacks such as prompt injection, tool chaining, privilege escalation, or impersonation. Maintain threat models and update defenses as new attack patterns emerge.
Governance, Change Control, and Permission Reviews
Enforce strict change control for adding tools or updating MCP server code. Require security review, version control, and rollback mechanisms. Periodically audit and revoke unused permissions or tools.
Compliance Implications and Emerging Regulatory Expectations
Although MCP is a relatively new technology, its reach and influence demand early attention from compliance professionals. Organizations deploying MCP servers must ensure:
- Auditability: All actions triggered by agents must be fully logged and traceable. Tool calls and resulting system changes should be attributable.
- Least privilege and segregation of roles: Autonomous AI operations must respect the same internal control principles as human operators.
- Change control and versioning: Any update to MCP servers or tool sets should follow formal review and testing workflows.
- Data protection / privacy laws: When MCP agents access personal or sensitive data, controls must enforce data minimization, purpose limitation, and retention policies in compliance with regulations such as GDPR or CCPA.
As MCP-based AI systems proliferate, regulatory bodies, auditors, and industry standards will likely expect that actions mediated by MCP servers are treated with the same rigor as those in traditional IT environments.