Log Management
Aggregate and quickly analyze your essential logs from multiple sources
Talk with our experts

Log Management
Aggregate and quickly analyze your essential logs from multiple sources
Customers Around the World
Real-time analysis
Quickly and Easily Review Logs
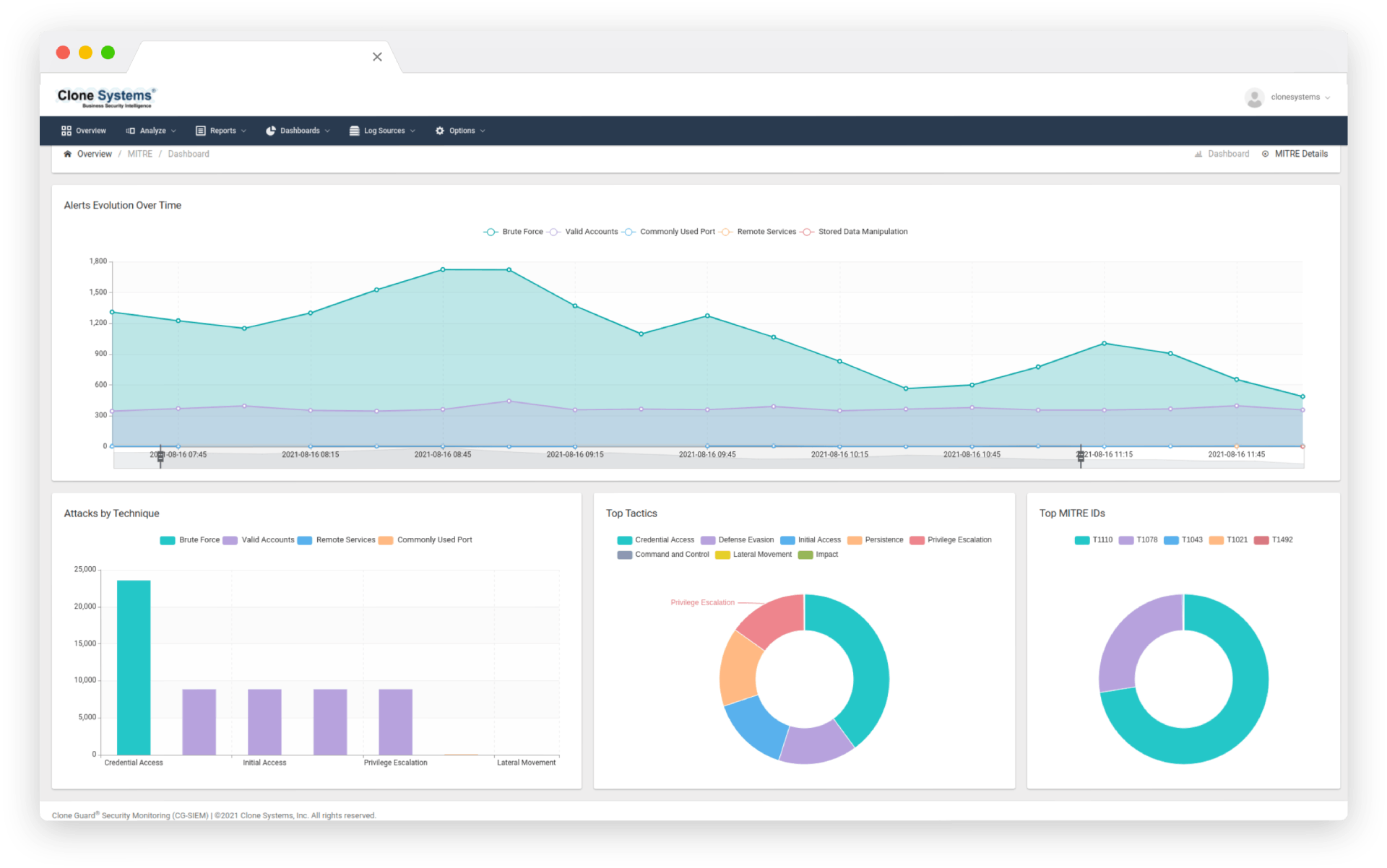
Log collection and storage with powerful parsing capabilities allow you to identify issues quickly. Real-time search and analysis, streamlining your ability to troubleshoot and perform postmortem analysis. Aggregate OS, application, network, endpoint, container, virtualization, and Cloud logs into a single portal.
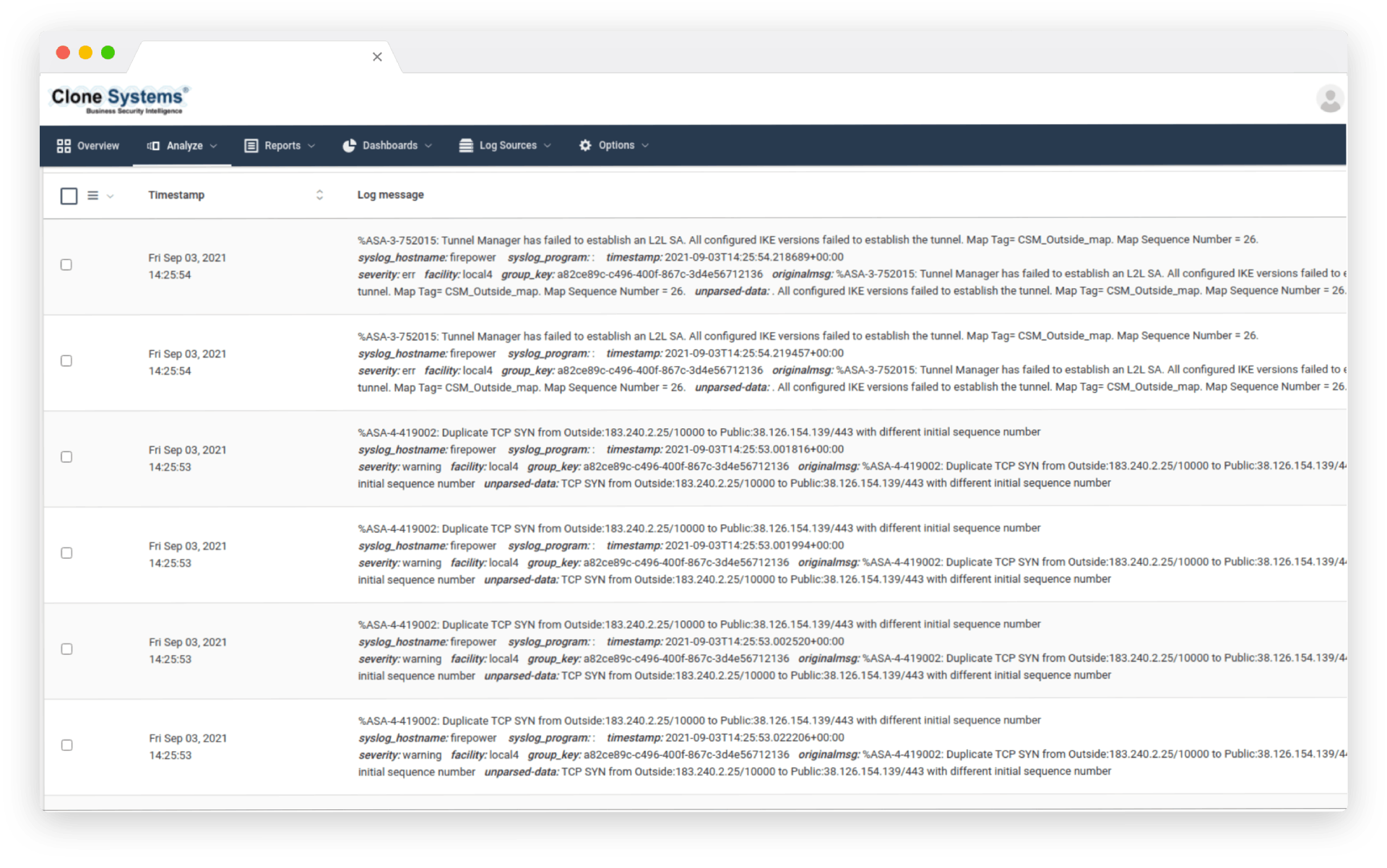
Real-time analysis
Quickly and Easily Review Logs
Log collection and storage with powerful parsing capabilities that allow you to easily identify issues. Real-time search and analysis, streamlining your ability to troubleshoot and perform postmortem analysis. Aggregate OS, application, network, endpoint, container, virtualization, and Cloud logs into a single portal.
24/7 monitoring
Empower Your Team
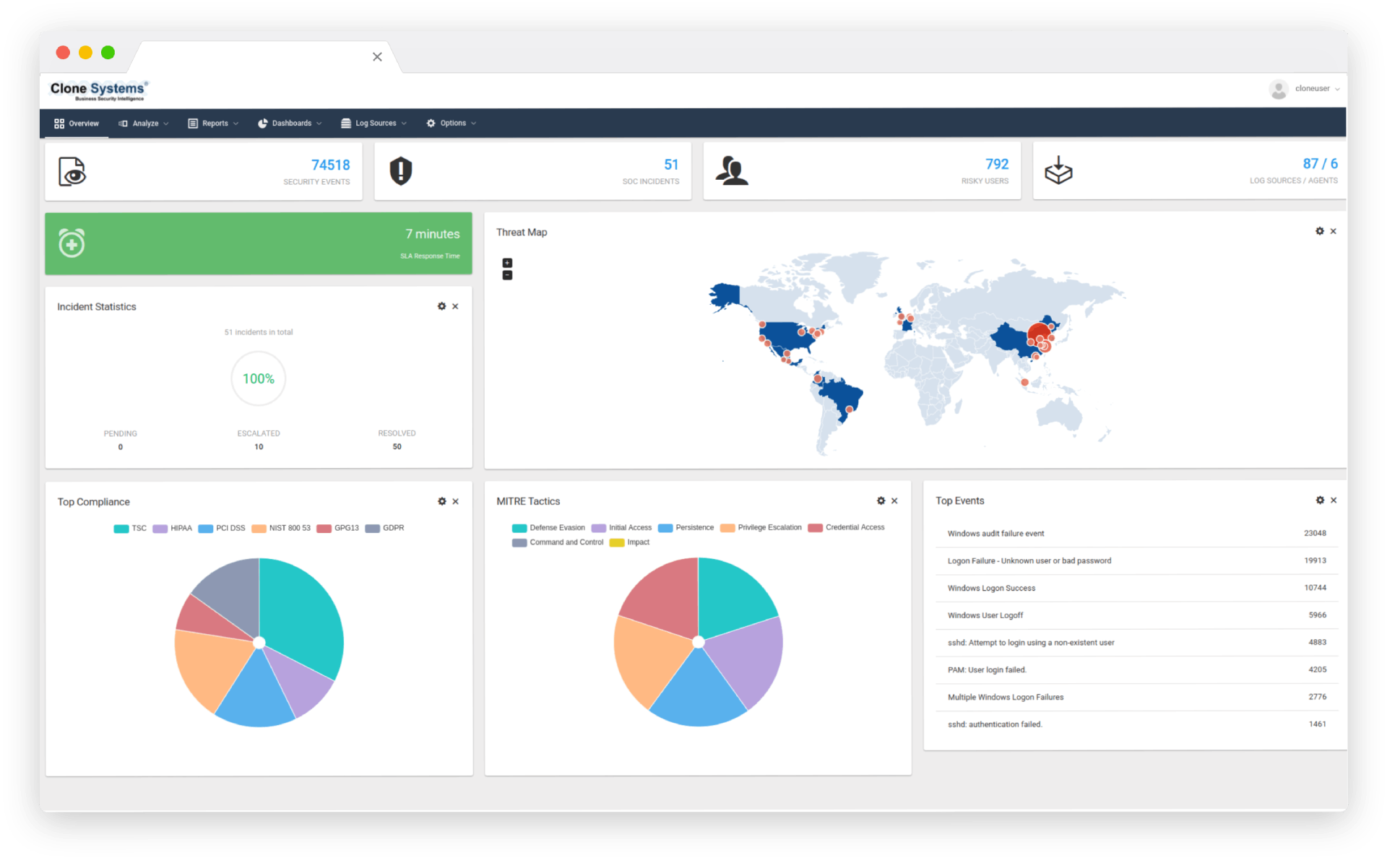
Monitoring and alerting capabilities to identify traffic that requires further investigation.
Security Operation Center triaging, escalating alerts, and providing guidance where needed 24/7.
Quickly identify key areas that need urgent attention, to facilitate troubleshooting and resolution.
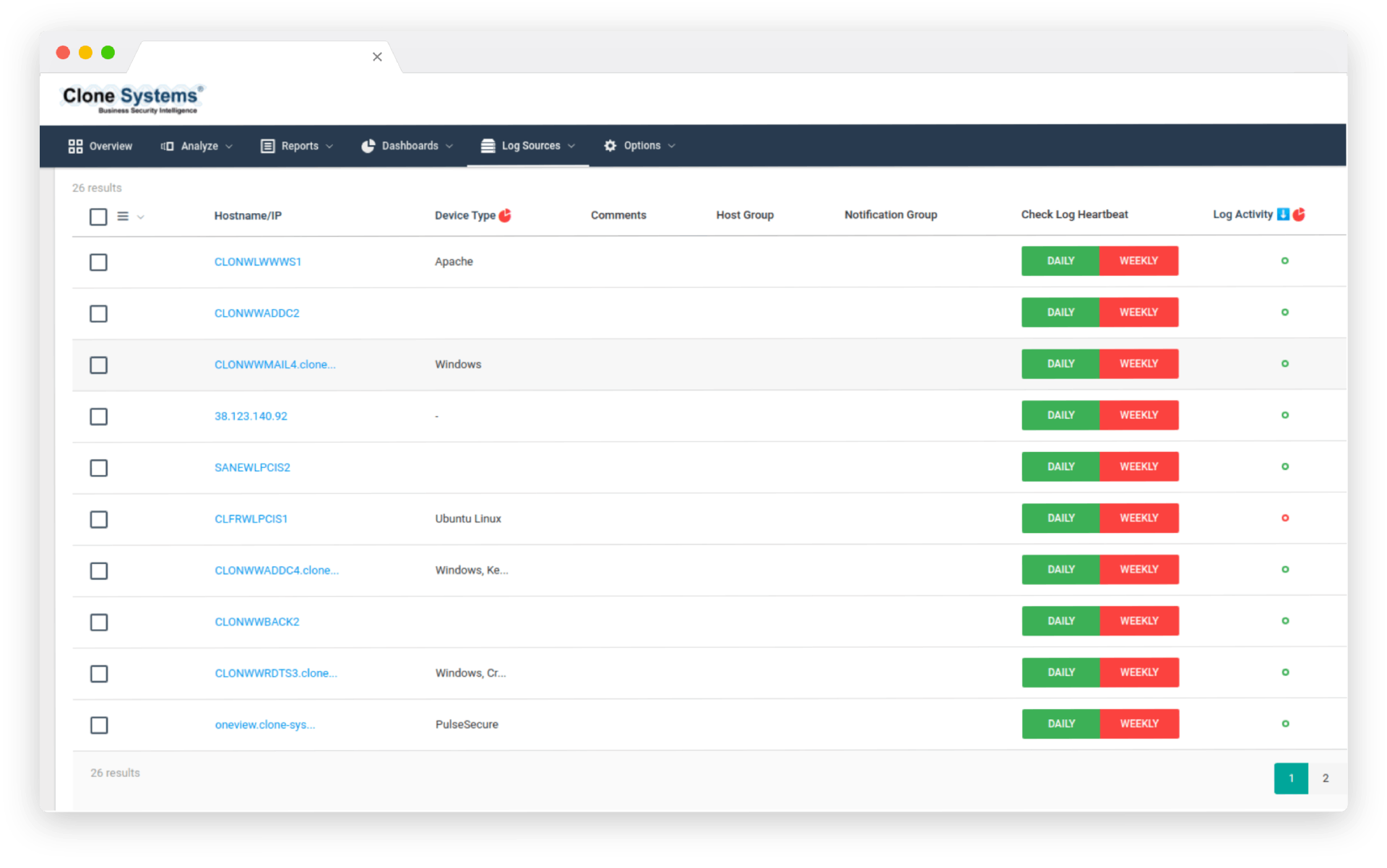
24/7 monitoring
Empower Your Team
Monitoring and alerting capabilities to identify traffic that requires further investigation. Security Operation Center triaging, escalating alerts, and providing guidance where needed 24/7. Quickly identify key areas that need urgent attention, to facilitate troubleshooting and resolution.
PCI, HIPAA, SOX, SOC2, GDPR
Maintain Your Compliance
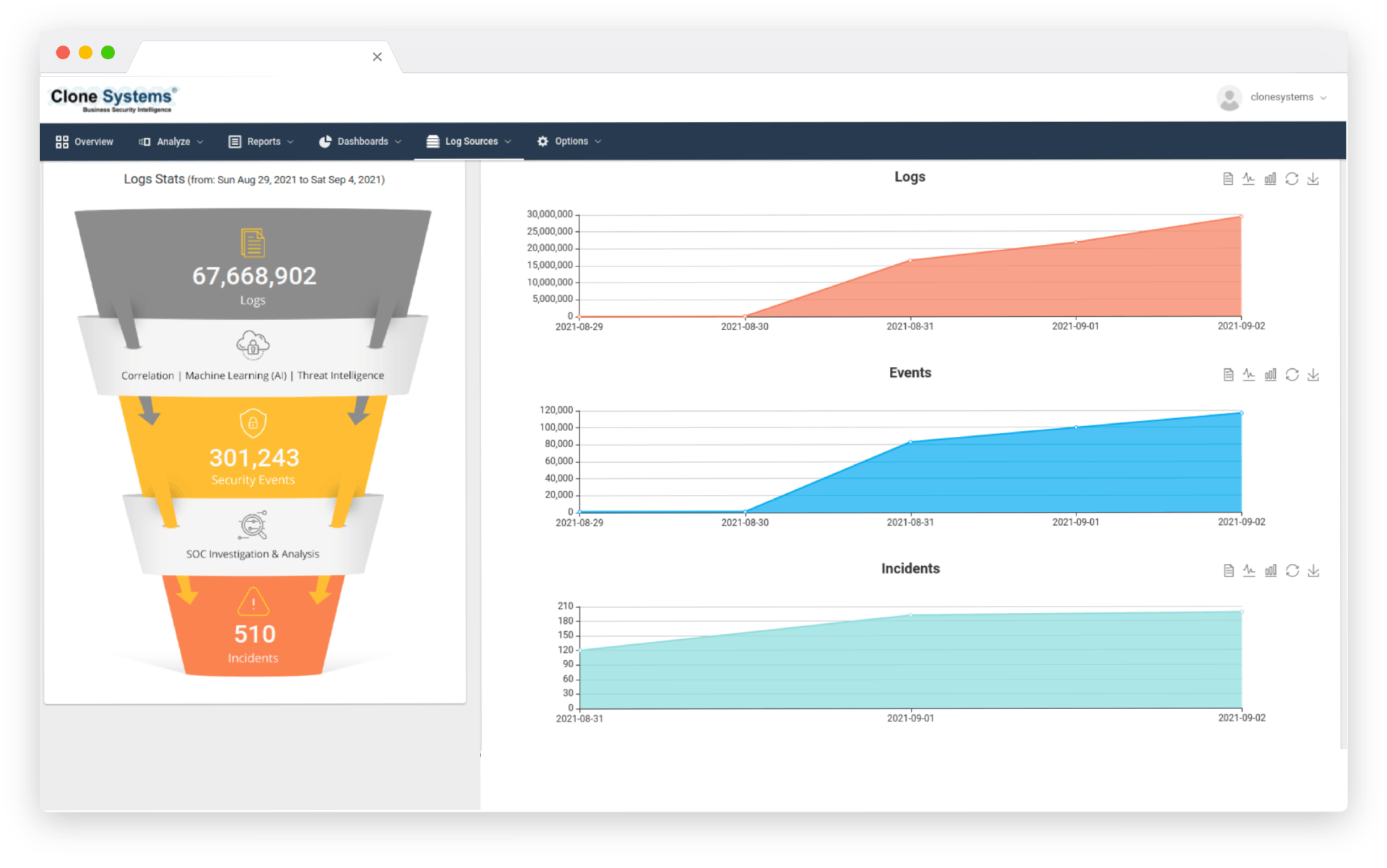
Maintain compliance with industry standards and regulations (PCI, HIPAA, SOX, SOC2, GDPR, and others) Detailed reporting of all security-related logs for any device and endpoint on your network. Offsite long-term storage and log data retention in PCI and GDPR-compliant data centers.
*Security Information and Event Management (SIEM) correlation available as an additional service
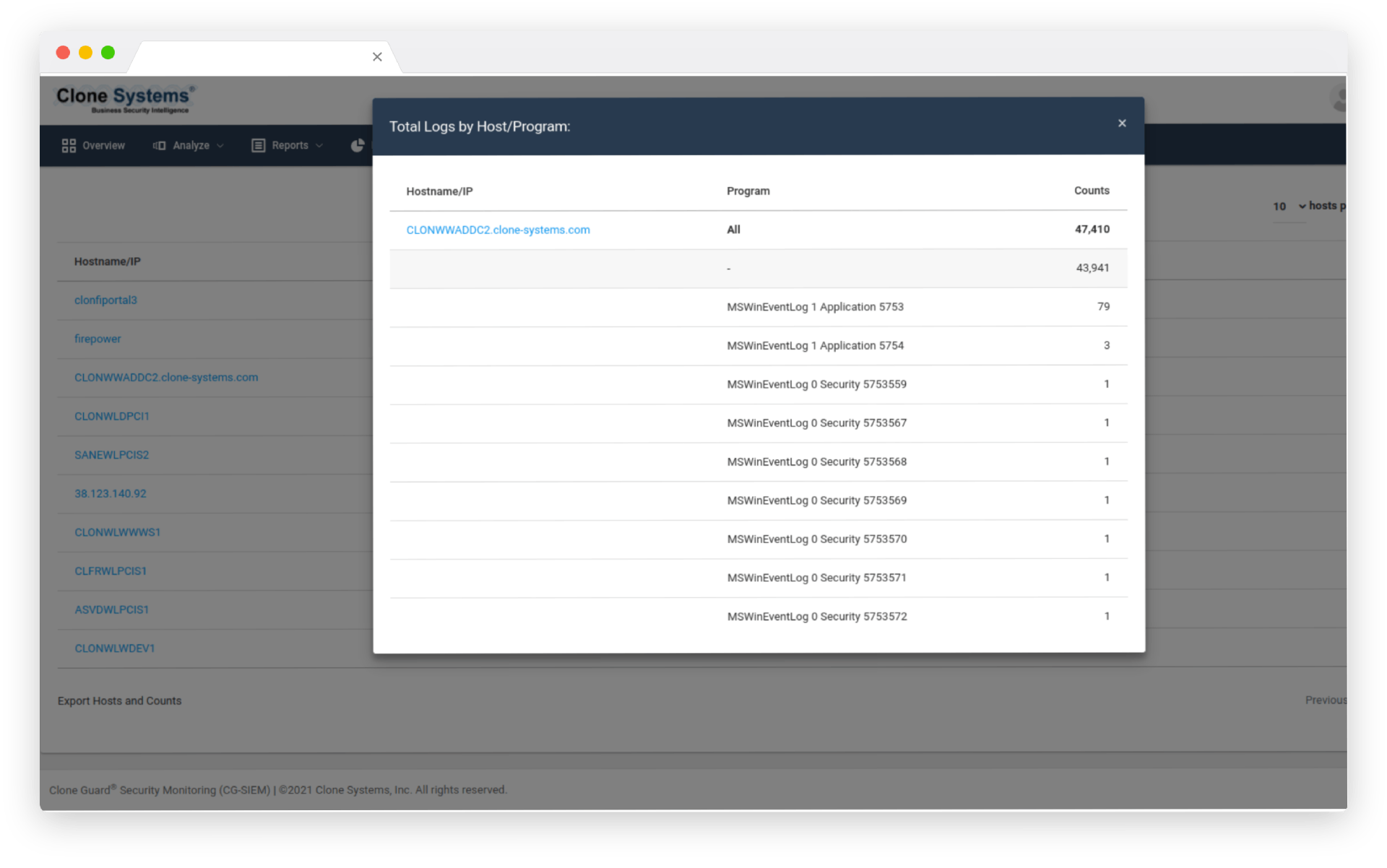
PCI, HIPAA, SOX, SOC2, GDPR
Maintain Your Compliance
Maintain compliance with industry standards and regulations (PCI, HIPAA, SOX, SOC2, GDPR, and others) Detailed reporting of all security-related logs for any device and endpoint on your network. Offsite long-term storage and log data retention in PCI and GDPR-compliant data centers.
*Security Information and Event Management (SIEM) correlation available as an additional service

LOG MANAGEMENT PRODUCT SHEET
Download the Log Management Product Sheet

How Log Management Works
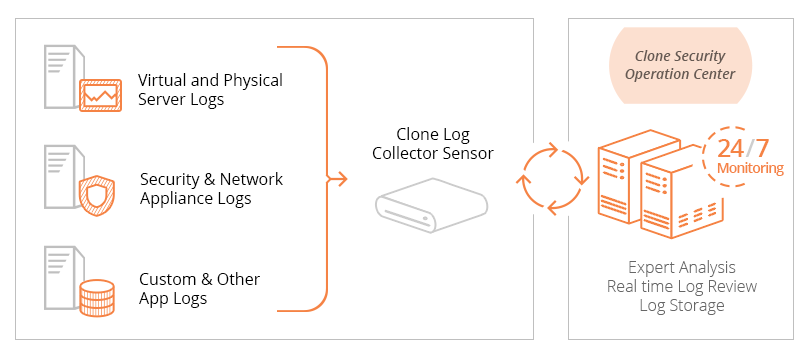
Our team of certified security engineers will work closely with you to review your current infrastructure and solutions and identify the recommended devices that should forward logs to maximize your ability to find vulnerabilities, identify suspicious activity, and troubleshoot your network.
A Log Management device will be configured according to your business requirements so that your team can install it within your network and begin the process of forwarding essential logs that will be parsed, normalized, classified, and categorized into a central repository.
We will then work closely with your team to train them on the intuitive Log Management solution so they can obtain a holistic view of security events across their network and quickly conduct real-time searching and analysis across a large volume of log data.
Our Security Operation Center (SOC) will consistently monitor the logs sent to the Log Management device to triage events and escalate alerts as needed 24/7 so your team can expedite troubleshooting and resolution of urgent events that require your attention.
Additionally, your logs will be securely archived on a nightly basis to Clone Systems enterprise data centers to comply with industry standards and regulations and to support any future disaster recovery effort or forensic investigation.