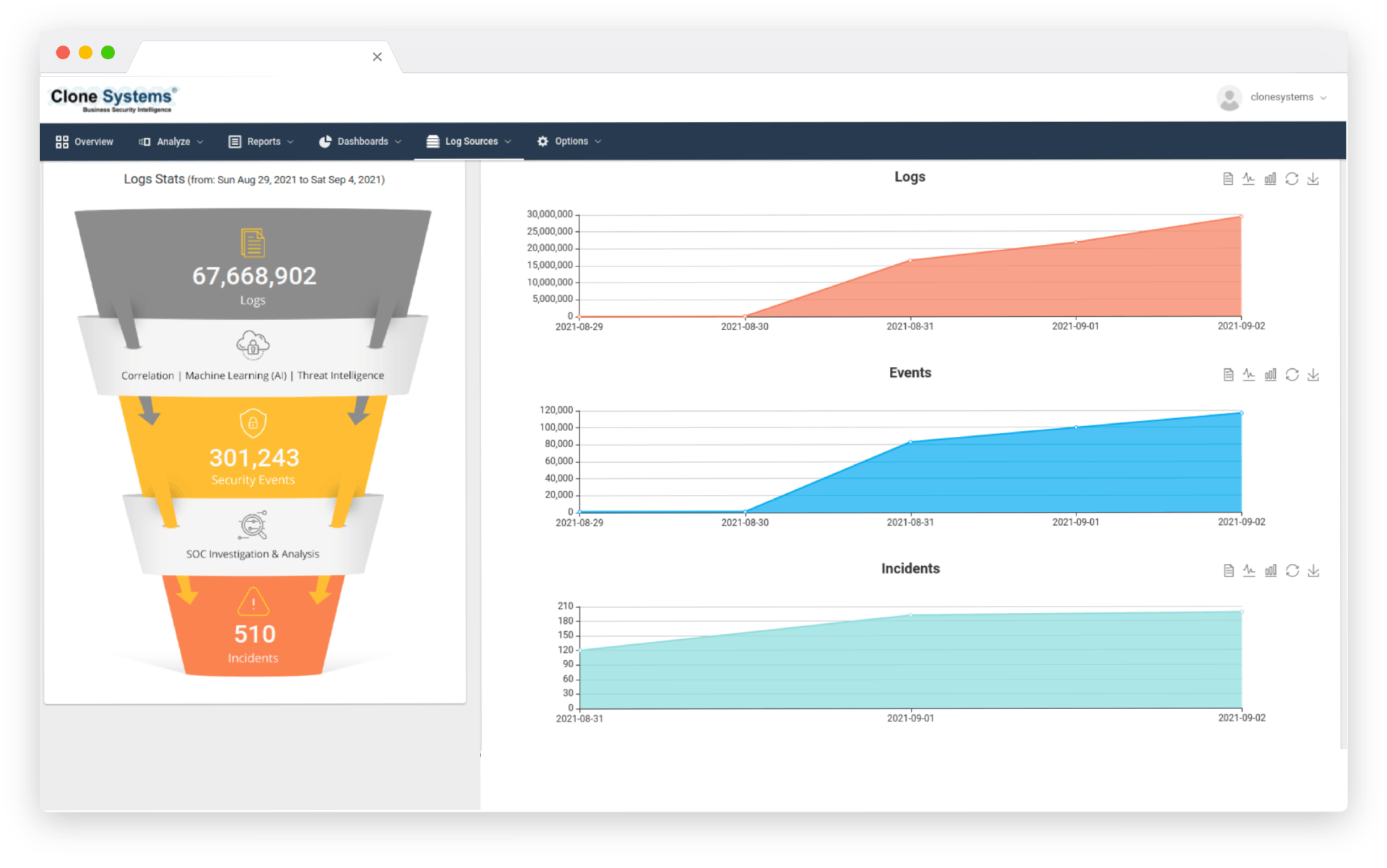
log management
Instructions for forwarding logs
Search for instructions for forwarding logs to your management service
Learn about Log Management
Aggregate and quickly analyze your essential logs from multiple sources
Schedule your Demo today!
No software to download or install.
Email us or call us at 1.800.414.0321.
