Understanding Load Balancers in PCI ASV Scanning
External vulnerability scanning is a required part of PCI DSS compliance for any organization that stores, processes, or transmits cardholder data. These scans must be conducted by an Approved Scanning Vendor (ASV) and are intended to identify vulnerabilities in internet-facing systems.
One of the most common reasons for failed or incomplete scans is the presence of load balancers. While load balancers are essential for performance and availability, they introduce specific challenges that must be addressed to ensure the scan is accurate and meets PCI requirements.
As an ASV, we frequently encounter these issues across environments of all sizes. This article explains how load balancers affect PCI ASV scanning, what merchants need to watch for, and how to handle it effectively.
What Is a Load Balancer
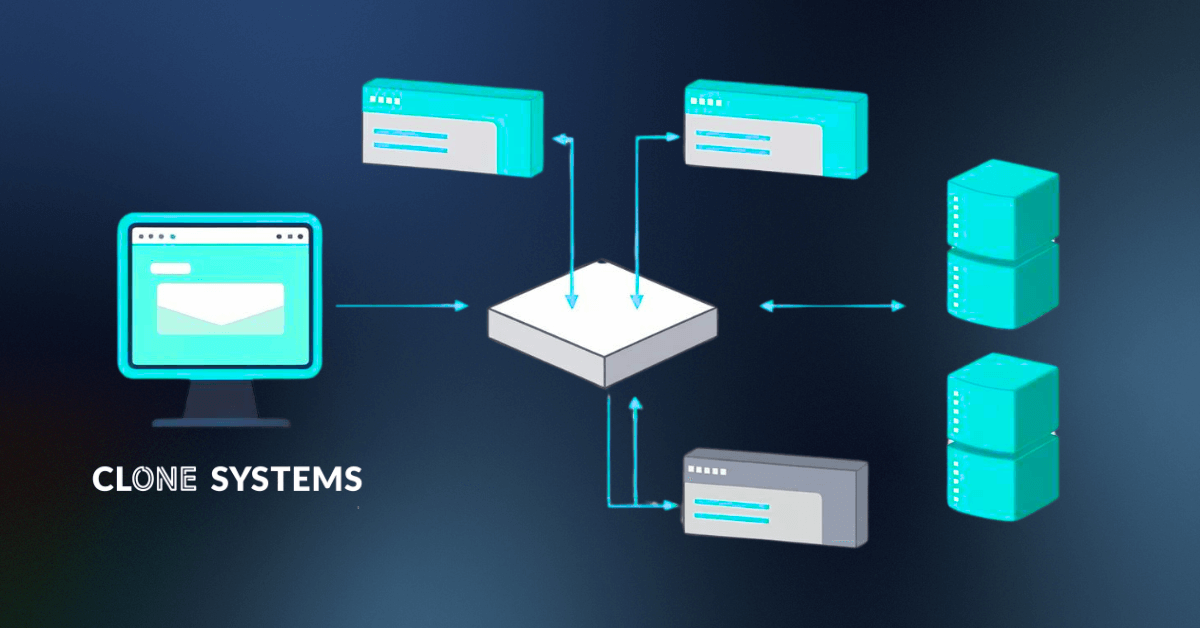
A load balancer is a system that distributes incoming network traffic across multiple backend servers. This allows an application or website to stay available and responsive under varying load conditions. Load balancers can operate at the network layer or the application layer and are commonly found in modern, cloud-native and high-availability environments.
Common Load Balancer Technologies
Organizations often use both traditional and cloud-based load balancers. Examples include
-AWS Elastic Load Balancer (ELB), Application Load Balancer (ALB), and Network Load Balancer (NLB)
-Azure Load Balancer
-F5 BIG-IP
-HAProxy
-NGINX
-Citrix ADC
Additionally, platforms like Cloudflare provide DNS and HTTP-level load balancing features alongside performance and security services.
Load Balancer Challenges in PCI ASV Scanning
Load balancers impact how traffic reaches backend systems. When improperly handled, this can cause vulnerability scans to miss systems or return results that do not reflect the full environment.
Below are common challenges we see as an ASV
Inconsistent Results Across Nodes
When a load balancer distributes scanner traffic across multiple backend systems, those systems may have different software versions, patch levels, or configurations. If only one server is scanned, the others may go unchecked even though they serve live traffic.
Session Affinity or IP Stickiness
Some load balancers use source IP stickiness which routes all traffic from a specific IP to a single backend server. This behavior prevents the scanner from reaching other nodes in the environment and creates a blind spot.
Backend Systems Are Masked
In many environments, backend systems behind the load balancer are not directly reachable from the internet. If the scan is limited to the front-end endpoint, it may not reflect the vulnerabilities present across the entire infrastructure.
Shared IP Addresses Across Multiple Domains
It is common for multiple domains or subdomains to resolve to the same public IP address. While they may appear to be part of a single system, they often serve different applications or customer experiences. Each domain must be assessed individually if in scope for PCI.
Related Technologies: CDNs and WAFs
Content delivery networks and web application firewalls are also commonly deployed in front of origin servers. These services improve performance and security by caching content and filtering malicious traffic. Platforms like Cloudflare, Akamai, and Fastly often combine CDN, WAF, and load balancing features into a single service layer.
Although helpful, these technologies can interfere with ASV scans if they block traffic or obscure backend infrastructure. It is the merchant’s responsibility to ensure these systems do not prevent the ASV from scanning in-scope assets.
We have published a separate guide on how to properly allow scan traffic through WAFs or CDNs by whitelisting scanner IPs.
Who This Applies To
These scanning considerations are relevant for a wide range of merchants and service providers, particularly those operating in cloud-based or distributed environments. Common scenarios include
-Ecommerce platforms
-SaaS providers
-Retailers with multiple branded websites
-Payment gateways or hosted checkout services
-Organizations using CDNs or reverse proxies
-Multi-tenant or shared infrastructure environments
Even small businesses using managed hosting or scalable architecture may encounter these issues without realizing it.
Best Practices for PCI Scanning in Load-Balanced Environments
To ensure accurate, complete, and PCI-compliant scans, we recommend the following practices
Maintain a Clear Inventory
List all in-scope domains, subdomains, and IP addresses. Include any backend systems that serve customer-facing content or are reachable from the public internet.
Collaborate with Your ASV Early
Inform your ASV about the presence of load balancers, CDNs, or other routing layers in your environment. Provide documentation about how traffic flows through these components.
Scan by IP Address When Applicable
If backend systems have public IP addresses that are distinct and reachable, scanning each IP directly ensures all nodes are tested regardless of load balancing behavior.
Use Custom Hostnames for Testing
You may configure temporary or internal-use DNS records to point directly to each backend server. This approach allows the ASV to scan each system individually even when public-facing traffic is routed through a single domain.
Disable Session Affinity if Feasible
Where possible, disable source IP stickiness during the scan window. This allows scanner traffic to reach multiple backend nodes. If this is not possible, discuss alternate methods with your ASV.
Document Load Balancer Configuration
Maintain internal records describing how traffic is distributed, what health checks are used, and which systems are included in the backend pool. This helps ensure transparency and can support your compliance documentation during audits.
Verify Scan Coverage Post-Assessment
Once the scan is complete, review the results with your ASV to confirm that all intended systems were tested and that backend nodes were not excluded due to routing behavior.
PCI DSS Expectations and Compliance Requirements
The PCI DSS requires that all externally accessible systems within the cardholder data environment are included in the quarterly ASV scan. This includes systems behind load balancers or reverse proxies if they are accessible from the public internet or impact the security of cardholder data.
Organizations are also responsible for validating the scope of their environment regularly and ensuring that scan results reflect the entire in-scope infrastructure. Load balancers and related technologies must not obscure visibility or prevent proper testing.
Final Thoughts
Load balancers play a critical role in maintaining system availability and performance but they can introduce significant challenges when it comes to PCI ASV scanning. Incomplete scans can lead to failed compliance, increased risk exposure, or gaps in security visibility.
The good news is that these issues are solvable. With the right planning, visibility, and partnership with your ASV, you can ensure that all systems are scanned properly, even in complex or load-balanced environments.
If you need help determining whether your infrastructure is being properly scanned, or if you are experiencing issues related to load balancers, contact our team. We work with organizations of all sizes to help them navigate the complexities of PCI scanning with confidence and clarity.