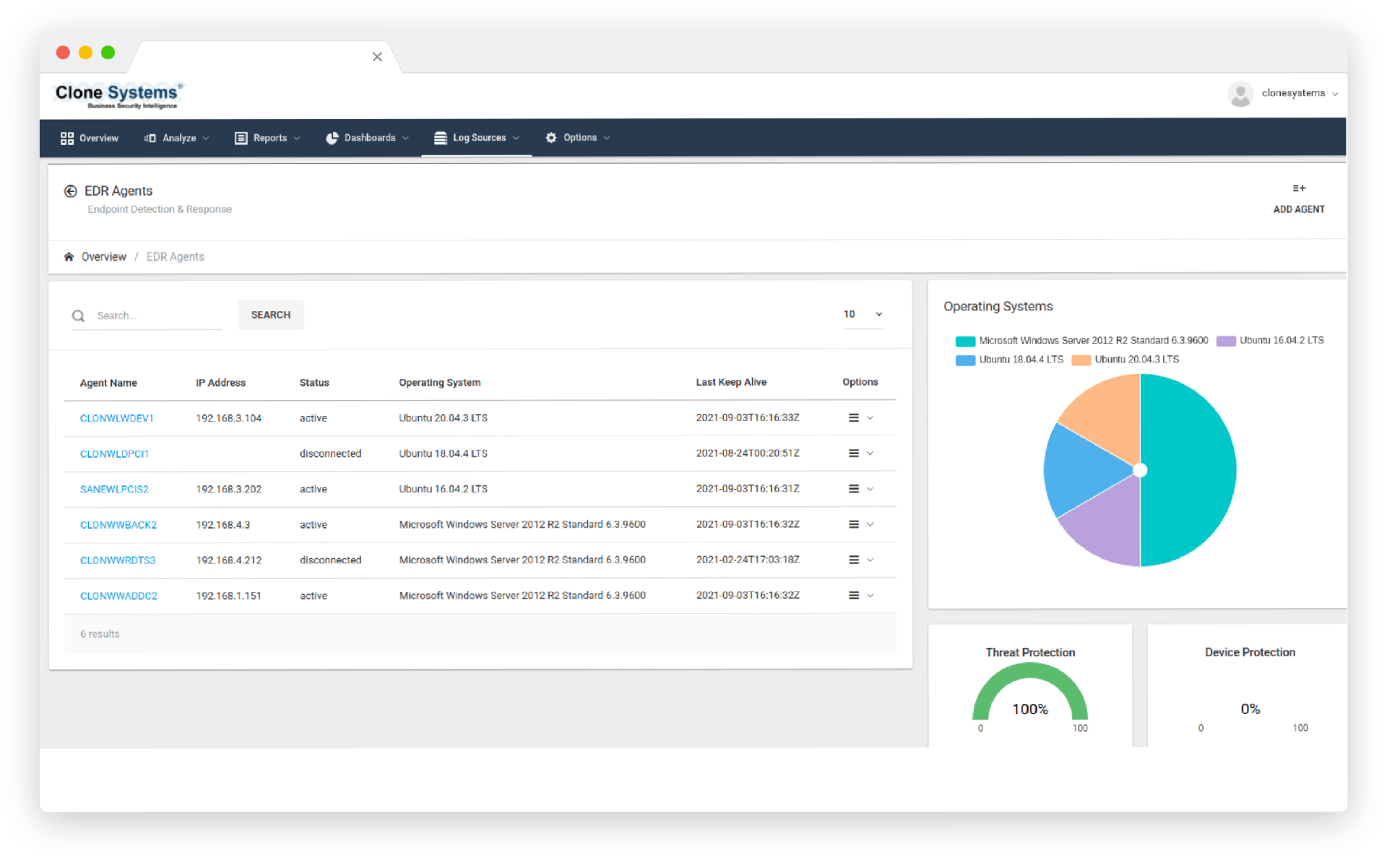
Extended Detection and Response (XDR)
Detect and respond to malicious operations across the IT stack, including endpoint, network, and cloud deployments.
Talk with our experts

Extended Detection and Response (XDR)
Detect and respond to malicious operations across the IT stack, including endpoint, network, and cloud deployments.
Customers Around the World
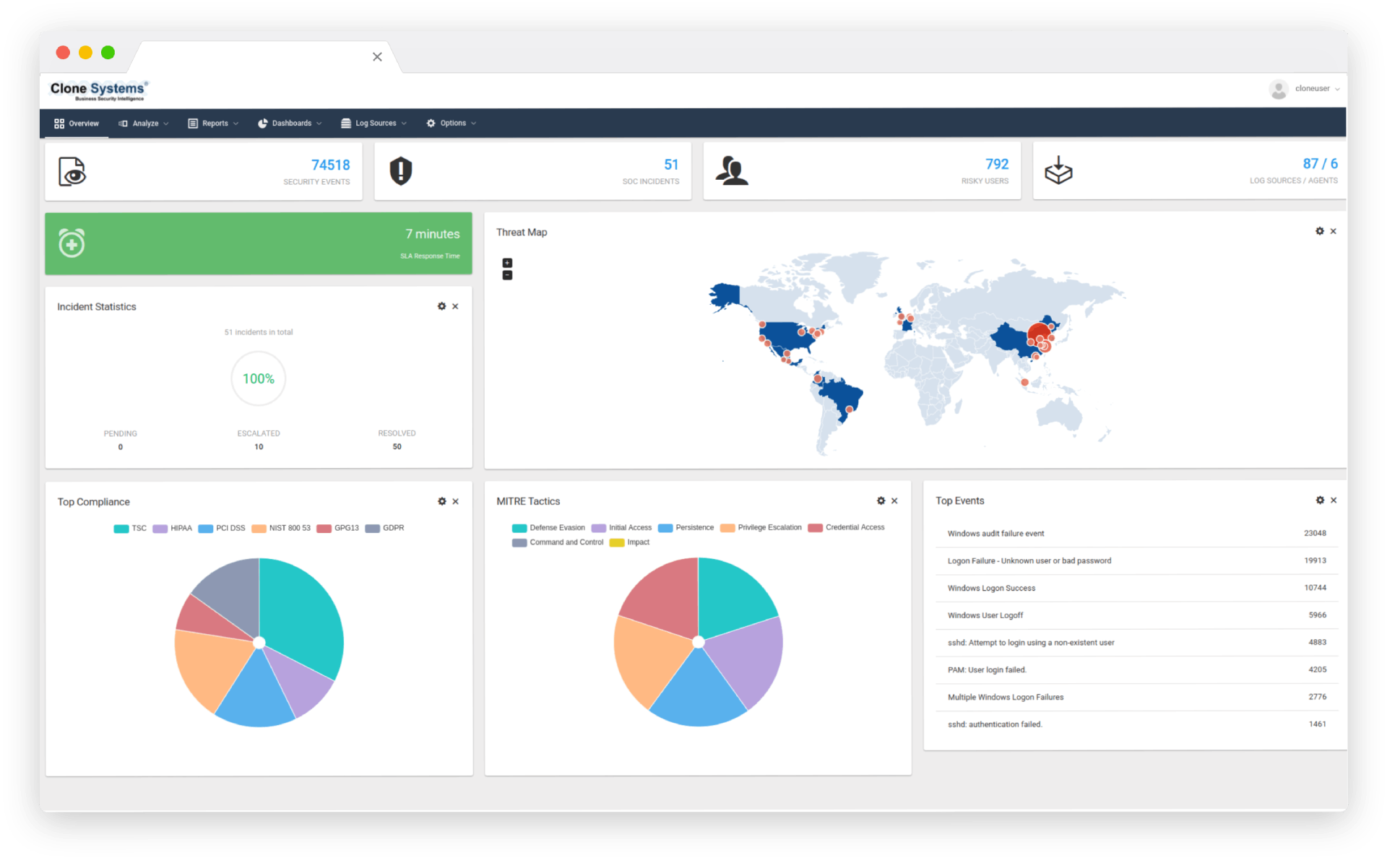
Compromise Analytics
Beyond Endpoint Security
Never lose sight of the attacker thanks to a unified view of cloud, endpoint, network, and log data that reveals threats and anomalous behavior.
Use both Indicators of Compromise and Behavior Analytics, to discover the most subtle signs of compromise from across your organization’s networks.
Compromise Analytics
Beyond Endpoint Security
Never lose sight of the attacker thanks to a unified view of cloud, endpoint, network, and log data that reveals threats and anomalous behavior. Use both Indicators of Compromise and Behavior Analytics, to discover the most subtle signs of compromise from across your organization’s networks.
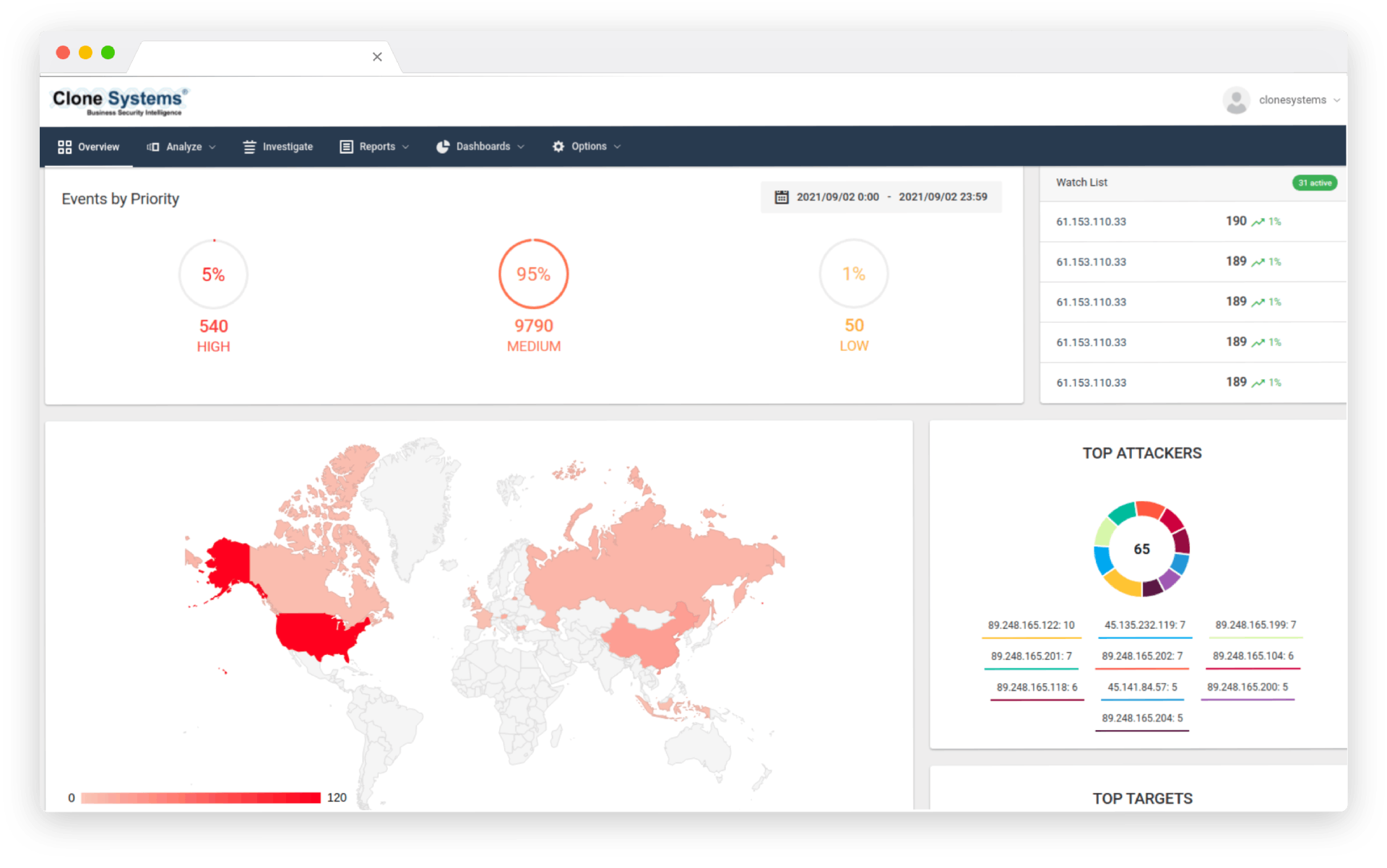
effective detection and response
Adaptive Response
Reduce Mean Time to Response (MTTR) across all networks with automated and guided one-click mitigation via SOAR that eliminates the need for complex queries.
Eliminate impediments to effective detection and response, such as log management and data collection tasks, agent deployment and maintenance cycles, and convoluted data extraction and behavioral detection syntax languages.
effective detection and response
Adaptive Response
Reduce Mean Time to Response (MTTR) across all networks with automated and guided one-click mitigation via SOAR that eliminates the need for complex queries. Eliminate impediments to effective detection and response, such as log management and data collection tasks, agent deployment and maintenance cycles, and convoluted data extraction and behavioral detection syntax languages.

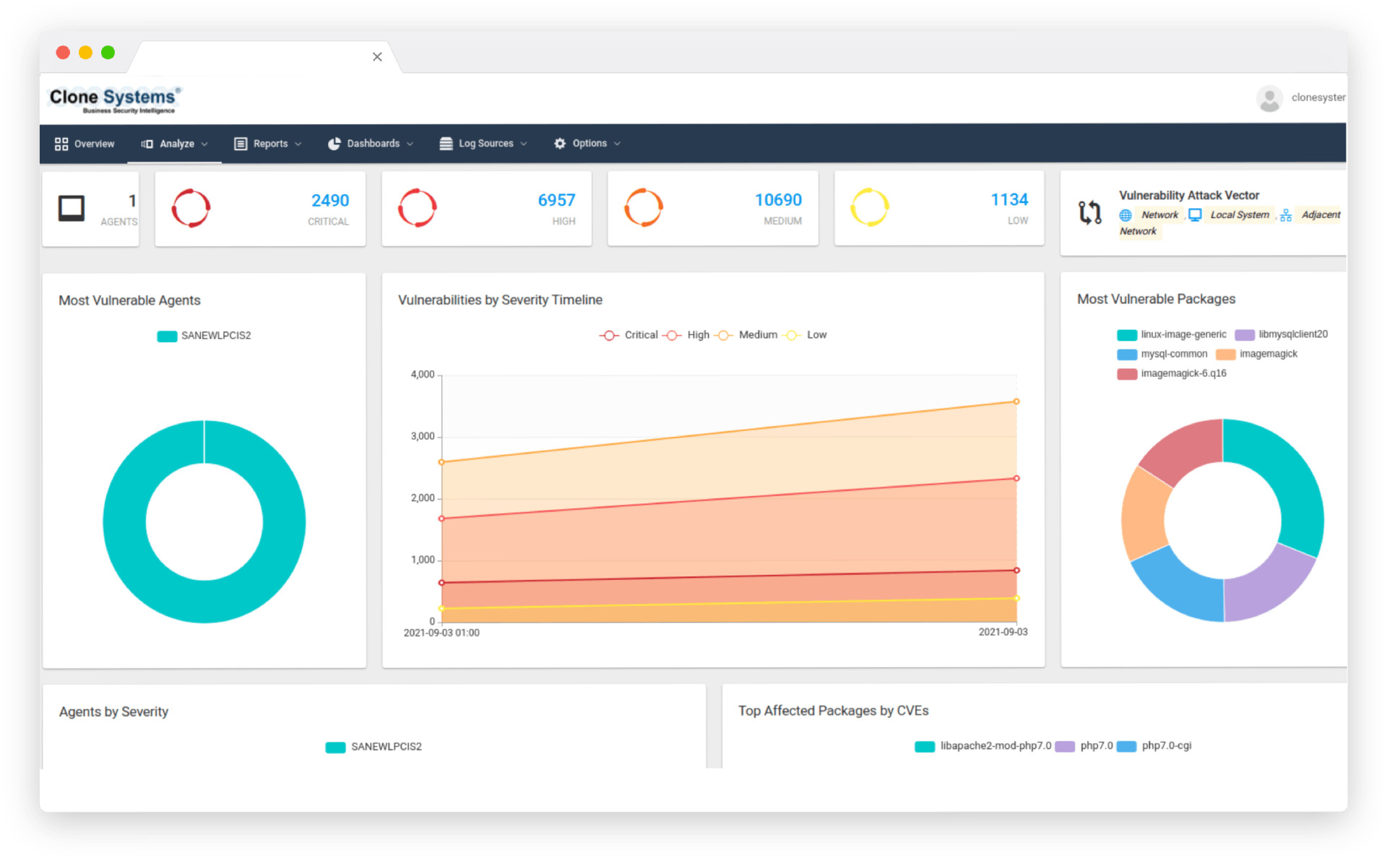
What is Extended Detection and Response (XDR)?

Extended Detection and Response (XDR) is a new cybersecurity service on the rise. It combines managed threat detection and response to protect organizations from cyber threats with endpoint protection and response.
It’s a one-stop shop for all things related to threat detection and response. Typically, security operations teams deploy dozens of Cyber Security tools to prevent, detect, and remediate threats.
XDR services give businesses end-to-end visibility into data across their network, endpoints, and security technologies, allowing them to identify and respond to threats quickly.
Businesses hire XDR service providers to aggregate and monitor their data from all available sources, analyze the data, and respond quickly to alerts to protect the company and reduce risk.