Beyond the Perimeter: Why Zero Trust is Your Next Cybersecurity Imperative
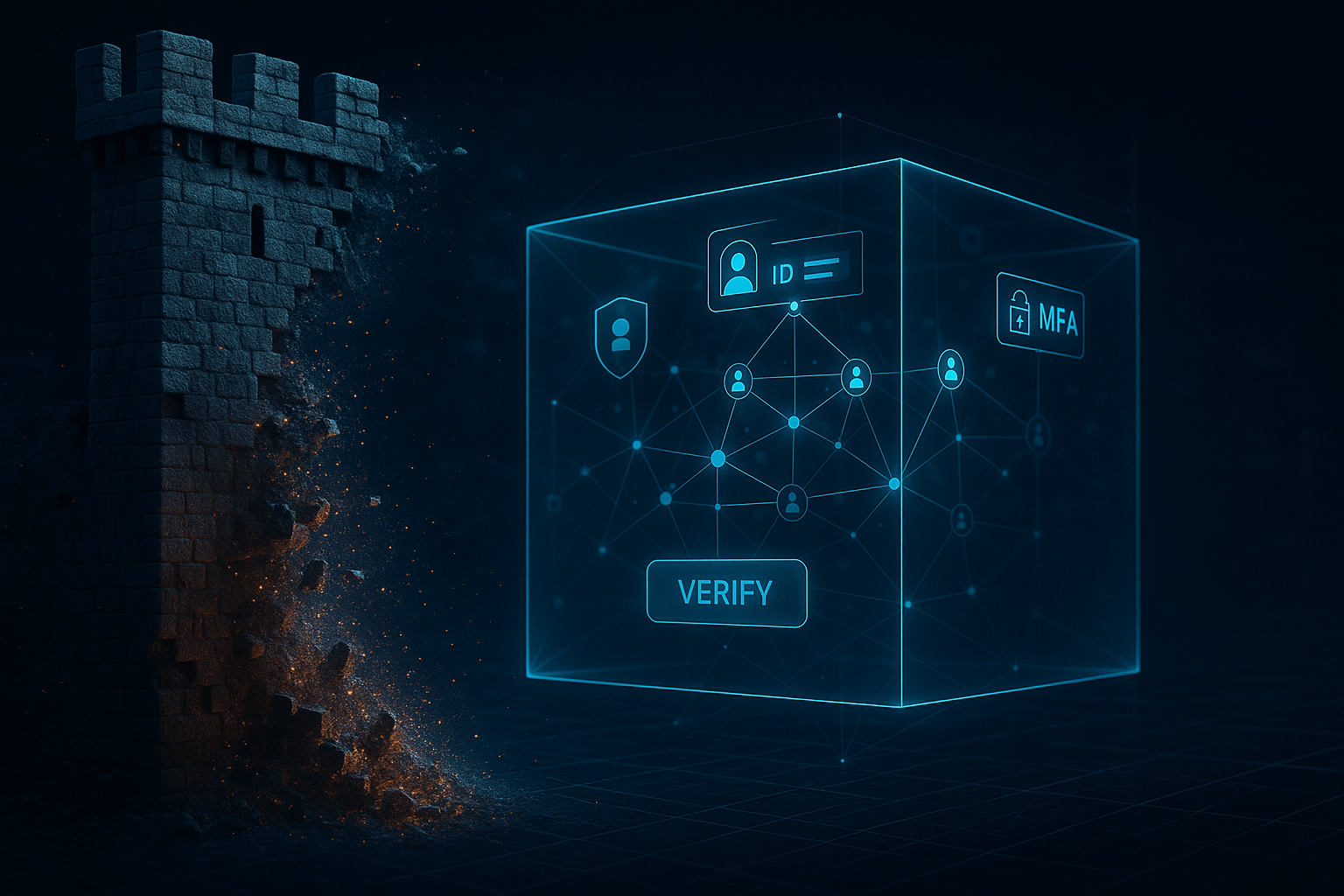
In today’s increasingly interconnected digital world, relying on old-school security models, like the traditional ‘castle-and-moat’ approach, just doesn’t cut it anymore. Cyber threats are evolving incredibly fast, making it clear that simply trusting everything inside your network is a risky business.
This is precisely where Zero Trust Architecture (ZTA) steps in; not just as a trendy term, but as a fundamental shift in how organizations think about security. At Clone Systems, we believe that strong security isn’t just about ticking compliance boxes; it’s about building true resilience. Let’s explore why Zero Trust is quickly becoming the bedrock of modern cybersecurity strategies and how it can truly strengthen your defenses against both current and future threats.
What Exactly is Zero Trust?
At its core, Zero Trust operates on a simple yet powerful principle: “never trust, always verify.” This is a significant departure from older security models that assumed everything inside the network was inherently safe. Instead, Zero Trust assumes that a breach is always possible and meticulously verifies every user and device before granting access to any resource, regardless of whether they are connecting from within or outside the corporate network. This fundamental shift is absolutely critical now, especially with the rise of remote work, widespread cloud adoption, and mobile devices blurring the traditional network boundaries.
It’s important to understand that Zero Trust isn’t a single product or technology; it’s a comprehensive security framework built around several key concepts:
- Micro-segmentation: This involves breaking down security perimeters into much smaller, isolated zones. The idea is to limit access to specific parts of the network, so if one area is compromised, the damage is contained.
- Multi-Factor Authentication (MFA): This means requiring more than one way to prove identity, like a password combined with a code from your phone. It’s a crucial layer of defense.
- Least Privilege Access: Users are only given the bare minimum access they need to do their jobs, and nothing more. This significantly reduces the potential impact of a compromised account.
- Continuous Monitoring: The network is constantly watched, with all traffic and user behavior analyzed for any signs of suspicious activity. This vigilance helps catch threats in real-time.
- Device Trust: Every device trying to connect—whether it’s a laptop, tablet, or smartphone—is thoroughly checked for its security posture and compliance before it’s allowed access.
By diligently applying these principles, organizations can dramatically shrink their attack surface and prevent attackers from moving freely within their networks. This proactive and vigilant approach is absolutely essential for keeping sensitive data safe and ensuring business operations continue smoothly.
Why Zero Trust Now? The Shifting Threat Landscape
The need for adopting Zero Trust has become more pressing than ever. The cybersecurity landscape is constantly changing, bringing with it new and increasingly sophisticated threats. Here are some key reasons why Zero Trust is no longer just a good idea, but a critical necessity:
- The Explosion of Ransomware: Today’s ransomware attacks are incredibly sneaky and often manage to slip past traditional defenses. Zero Trust, with its precise access controls and constant verification, can significantly limit the damage by stopping ransomware from spreading throughout your network.
- The Remote Work Revolution: The massive shift to remote and hybrid work has essentially erased the old network boundaries. Employees are accessing company resources from all sorts of places and devices, making it impossible to rely solely on perimeter-based security. Zero Trust ensures that every single access request, no matter where it comes from, is properly authenticated and authorized.
- Embracing the Cloud: More and more organizations are moving their operations to the cloud, which introduces new security complexities. Cloud resources are naturally spread out, making a perimeter-focused approach impractical. Zero Trust extends security directly to your data and applications, no matter where they live in the cloud.
- Clever Phishing and Social Engineering: Even with the best training, people can still fall victim to phishing scams, leading to stolen credentials. Zero Trust helps reduce this risk by demanding continuous verification and flexible access policies, even if someone’s initial login details are compromised.
- The Threat of Supply Chain Attacks: Attackers are increasingly targeting third-party vendors and supply chains as a way to get into larger organizations. Zero Trust principles can be applied to how third parties access your systems, making sure that even trusted partners go through strict verification and have only the minimum access they need.
Clone Systems and Your Zero Trust Journey
Implementing a Zero Trust Architecture can feel like a huge undertaking, but many organizations discover that their existing security practices and specialized services can actually contribute quite a bit to this journey. Clone Systems, with its deep focus on crucial security areas, offers expertise that naturally aligns with the core principles of Zero Trust:
- PCI Compliance and Data Security: Zero Trust heavily emphasizes protecting sensitive data, a core tenet of PCI DSS. Our comprehensive PCI compliance solutions, including ASV scanning and reporting, help establish the foundational security controls necessary for a Zero Trust environment. By ensuring your cardholder data environment (CDE) is segmented and access is strictly controlled, we contribute directly to your Zero Trust maturity.
- API Security: As highlighted in our previous discussions, APIs are increasingly becoming attack vectors. Zero Trust extends its principles to API security by ensuring every API call is authenticated, authorized, and continuously monitored. Our API security expertise helps you implement robust controls that align with Zero Trust, preventing unauthorized access and data breaches through your application programming interfaces.
- Vulnerability Management and Penetration Testing: Continuous monitoring and assessment are vital components of Zero Trust. Our vulnerability scanning and penetration testing services provide crucial insights into your security posture, identifying weaknesses that could be exploited. This proactive identification and remediation of vulnerabilities are essential for maintaining the integrity of your Zero Trust framework.
- Identity and Access Management (IAM): While not explicitly listed as a service on your resources page, IAM is a critical component of Zero Trust. Our understanding of secure access practices, often derived from PCI compliance requirements, can guide organizations in strengthening their IAM policies to support least privilege and multi-factor authentication, key pillars of ZTA.
By understanding how your current security efforts and specialized services, like those provided by Clone Systems, fit into a Zero Trust framework, organizations can build a much stronger and more adaptable security posture. This integrated approach helps protect your assets and data more effectively, perfectly aligning with the core ideas of Zero Trust.
The Path Forward: Embracing a Zero Trust Mindset
Adopting a Zero Trust Architecture isn’t a quick fix or a one-and-done project; it’s an ongoing journey of constant improvement. It demands a fundamental shift in how we think about security—moving from simply trusting by default to explicitly verifying every single interaction. While getting started might seem a bit daunting, the long-term advantages—like significantly stronger security, a much lower risk of breaches, and improved compliance—far outweigh the initial effort.
In a world where cyber threats are always changing and getting more sophisticated, embracing Zero Trust is no longer just an option; it’s a strategic necessity for any organization truly serious about protecting its digital assets. By exploring these principles and understanding how they can be woven into your existing security measures, organizations can build a truly robust and adaptable security framework that stands strong against the challenges of today’s threat landscape.