Common Reasons for PCI ASV Scan Failures and How to Resolve Them
Quarterly PCI ASV (Approved Scanning Vendor) scans are a required part of maintaining PCI DSS compliance. While the threat landscape has evolved and scanning technologies have advanced, many organizations continue to encounter recurring issues that lead to failed scans. These issues are not typically the result of novel exploits, but rather systemic misconfigurations, lapses in visibility, or operational oversights that remain unresolved across environments.
Based on our experience as a long-standing Approved Scanning Vendor and Managed Security Services Provider, the following are the most common failure points we continue to see in 2025, along with practical guidance on how to remediate them effectively and sustainably.
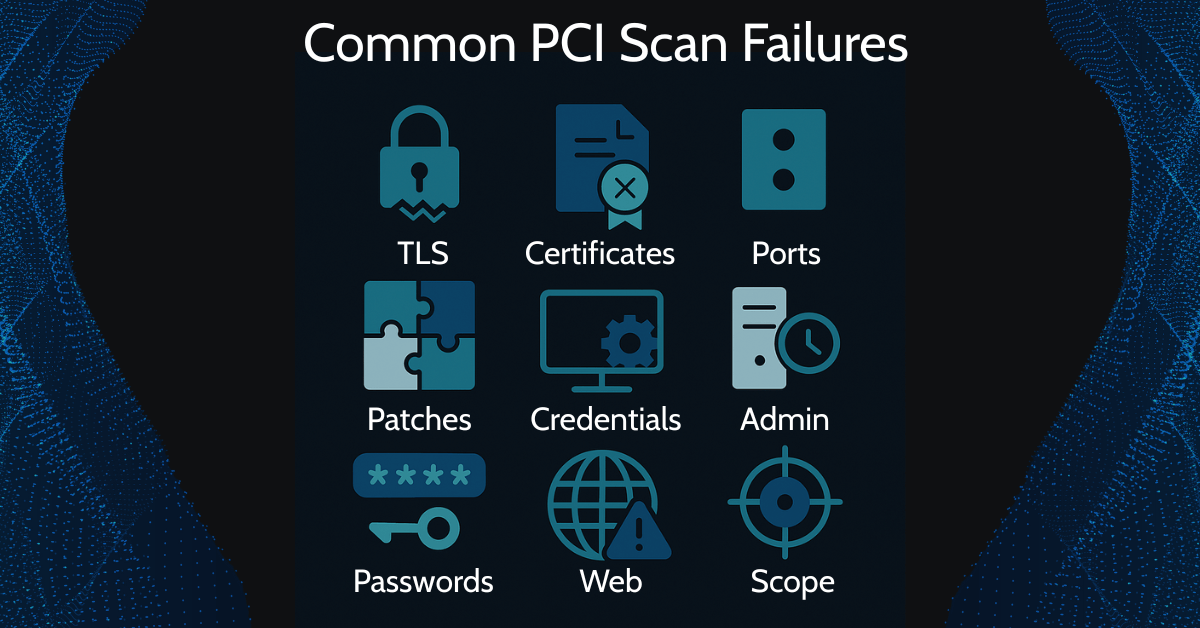
1. Deprecated SSL/TLS Protocols and Weak Ciphers
One of the most consistent causes of scan failure is the presence of insecure encryption protocols or cipher suites. Legacy protocols such as SSL 3.0, TLS 1.0, and TLS 1.1 are no longer accepted under current PCI DSS guidelines due to well-documented vulnerabilities. Even when TLS 1.2 or TLS 1.3 is implemented, weak cipher configurations can still result in a failed result.
Remediation Approach:
- Disable all protocols below TLS 1.2 across all public-facing systems.
- Limit cipher suites to only those that are strong, secure, and currently accepted by PCI DSS.
- Validate SSL/TLS implementations using industry tools such as SSL Labs.
- Apply consistent configuration standards across all relevant ports and subdomains.
2. Expired or Self-Signed Certificates
Digital certificates that are either expired or self-signed are not compliant with PCI DSS requirements for secure communications. These often appear in environments where certificate management is decentralized or not automated, leading to gaps that are easily identified during scans.
Remediation Approach:
- Replace all self-signed certificates with valid certificates from a recognized Certificate Authority.
- Establish centralized certificate management and expiration tracking.
- Confirm that all certificates are properly installed and valid across all exposed endpoints, including backup or non-primary domains.
3. Exposed Ports and Unsecured Services
Open ports and unnecessary services are frequently cited as causes of PCI scan failure. These may include legacy services such as FTP, Telnet, or unsecured management interfaces, all of which increase the organization’s external attack surface.
Remediation Approach:
- Conduct regular external and internal port audits.
- Disable services that are no longer required, and restrict access to critical services.
- Use host-based and network-based firewalls to apply access controls.
- Implement segmentation to isolate high-risk or administrative systems from general exposure.
4. Missing Security Patches and Known Vulnerabilities
Unpatched systems and software often result in scan failures, particularly when public vulnerabilities (CVEs) remain unremediated. This commonly applies to web servers, operating systems, application frameworks, and third-party libraries.
Remediation Approach:
- Maintain a formal patch management process with documented schedules and responsibilities.
- Subscribe to vendor advisories and monitor the National Vulnerability Database.
- Prioritize remediation based on CVSS severity scores and exposure.
- Ensure patching covers cloud-hosted assets and any containerized workloads in scope.
5. Public Access to Administrative Interfaces
Administrative dashboards and management consoles that are accessible from the public internet, such as phpMyAdmin or open RDP ports, frequently lead to noncompliance findings in ASV scans. These are often exposed unintentionally or remain accessible after temporary configurations are not reversed.
Remediation Approach:
- Remove administrative interfaces from public access whenever feasible.
- Restrict access via VPNs, bastion hosts, or dedicated management networks.
- Enforce multi-factor authentication and IP-based access control for any interfaces that require external access.
- Routinely validate external exposure using network reconnaissance tools.
6. Unmanaged or Forgotten Assets
Legacy servers, development environments, and decommissioned systems are often overlooked but still reachable from the internet. These environments tend to lack up-to-date patches or hardened configurations and are commonly flagged during scans.
Remediation Approach:
- Conduct asset discovery on a continuous basis using automated tools.
- Maintain an accurate inventory of in-scope and publicly exposed systems.
- Remove or isolate systems that are no longer in use.
- Implement change management processes to prevent the reintroduction of unmanaged assets.
7. Default Credentials and Weak Authentication Practices
Systems configured with default passwords or easily guessable credentials present a significant risk and are commonly detected during external scans. These findings often appear in SNMP configurations, router interfaces, or web administration panels.
Remediation Approach:
- Remove all vendor-supplied default credentials before deployment.
- Enforce strong password policies and implement credential rotation procedures.
- Centralize authentication where possible, using role-based access control.
- Where supported, apply multifactor authentication on all administrative systems.
8. Application-Level Vulnerabilities
Web application vulnerabilities remain one of the most significant contributors to PCI scan failures. Common issues include SQL injection, cross-site scripting, and insecure file access mechanisms, all of which can be exploited to compromise sensitive systems.
Remediation Approach:
- Integrate secure development practices into the software development lifecycle.
- Conduct regular dynamic (DAST) and static (SAST) application testing.
- Schedule manual penetration testing for any externally accessible, business-critical applications.
- Validate that remediation efforts are tracked and re-tested prior to the next scheduled scan.
9. Improper or Incomplete Scan Scoping
Failures sometimes occur not because of technical issues, but because of misalignment between what is scanned and what should have been in scope. This includes failing to include cloud-hosted assets, scanning the wrong IP ranges, or lacking proper authorization to scan critical systems.
Remediation Approach:
- Define scope in collaboration with your ASV and internal stakeholders.
- Ensure all systems that store, process, or transmit cardholder data are accounted for.
- Provide documentation and firewall access to ensure uninterrupted scanning.
- Update scope definitions as infrastructure or third-party dependencies change.
Recommendations for Ongoing Compliance
Most PCI scan failures can be avoided through consistent security hygiene and structured remediation workflows. Organizations should approach quarterly scanning as part of a continuous security posture rather than as a periodic compliance exercise.
We recommend the following practices to maintain readiness:
- Conduct internal pre-scan reviews prior to ASV engagements
- Establish a remediation response plan for handling findings efficiently
- Maintain centralized oversight across multi-location or multi-cloud environments
- Engage with your ASV regularly to validate scope and align on remediation expectations
Final Note
The persistence of these failure types underscores the importance of visibility, governance, and consistent execution. While the underlying issues are not new, they remain prevalent due to increasing infrastructure complexity, decentralized IT ownership, and incomplete remediation practices.
Organizations that proactively address these areas not only reduce compliance risk, but also significantly strengthen their overall security posture.